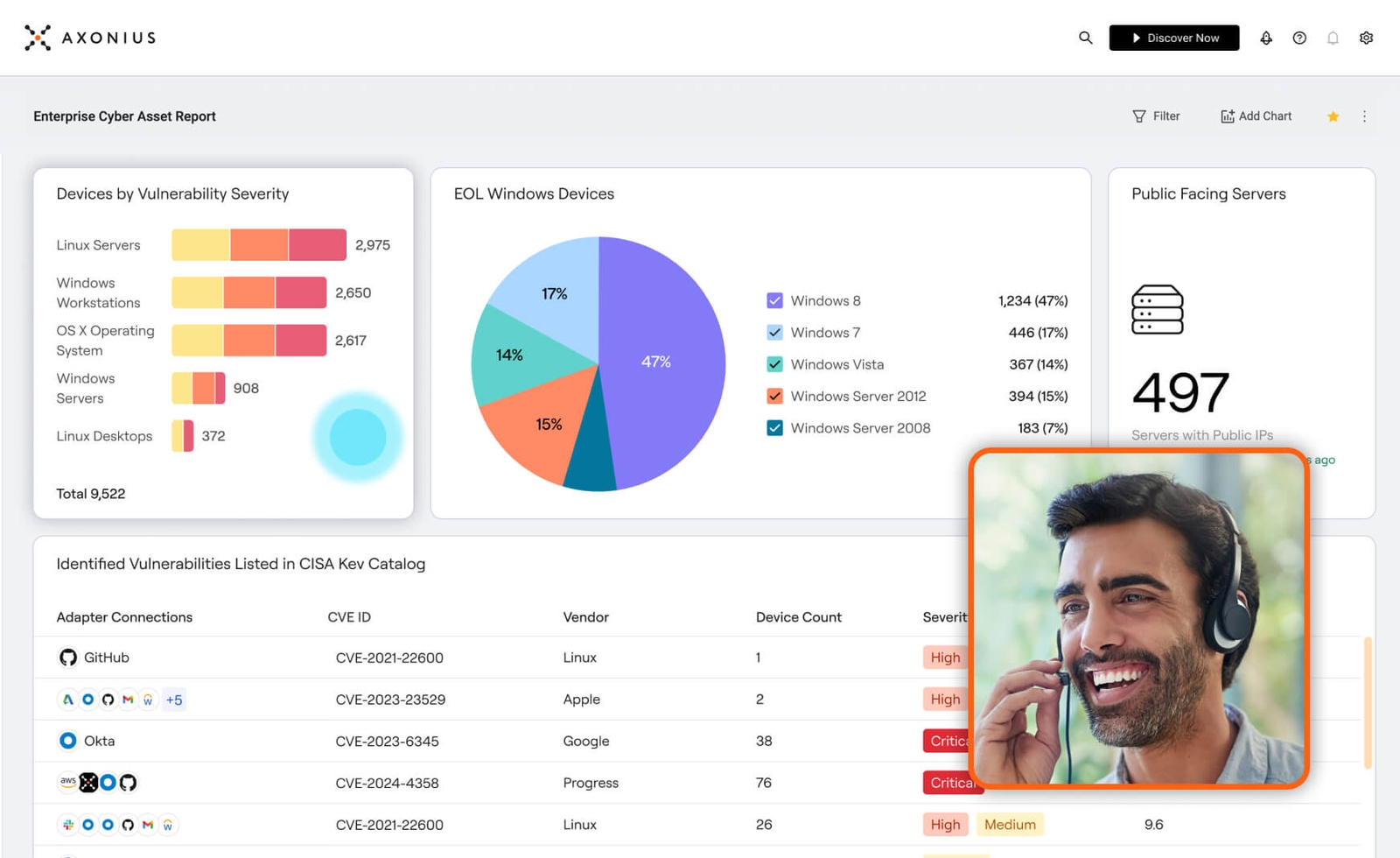
Ground investigations in the truth
Start every investigation with fully enriched and contextualized asset data. Axonius provides a unified view of your environment, ensuring you know exactly what assets exist, their relationships, and their risk profile—so you can act with confidence.




.png?width=950&auto=webp&format=jpg&disable=upscale)