AXONIUS PLATFORM
Identities
Transform fragmented identity data into actionable insights – bringing core discovery, lifecycle, governance, and posture management efforts together in one place to strengthen your IAM program resilience.
Consolidated identity actions from end-to-end
Axonius equips teams with the tools to optimize identity operations, unifying data from every downstream system and application with high granularity. Eliminate silos, reduce sprawl, and take swift, informed action across the entire identity lifecycle.
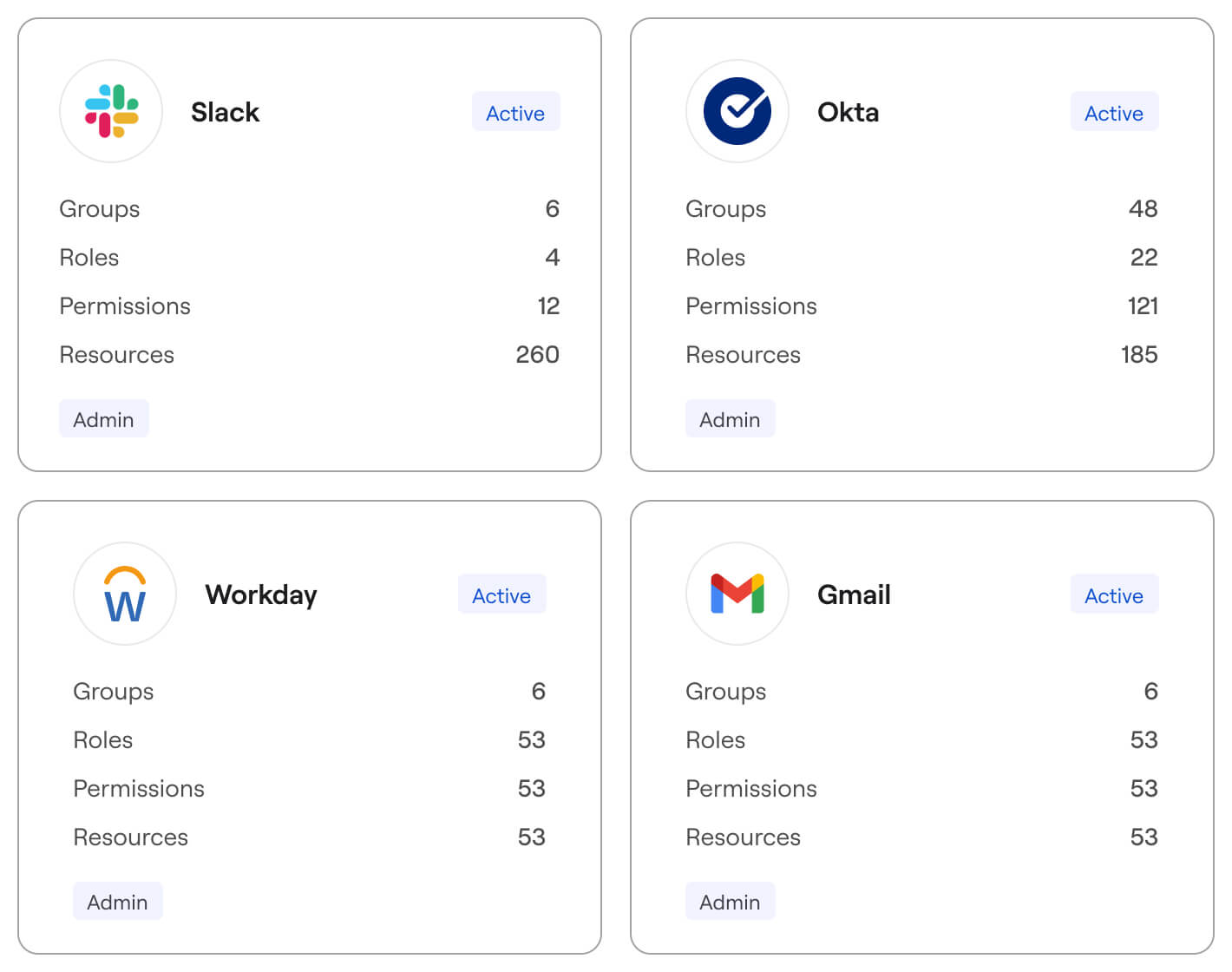
Illuminate all identity artifacts and blind spots
Gain complete visibility into your identity fabric by continuously discovering all human and machine/non-human identities across your cloud, on-prem, and hybrid environments. Axonius bi-directionally integrates with your systems and applications to sync accounts, roles, policies, entitlements, permission sets, and resources – ensuring you never miss a single identity in your environment.
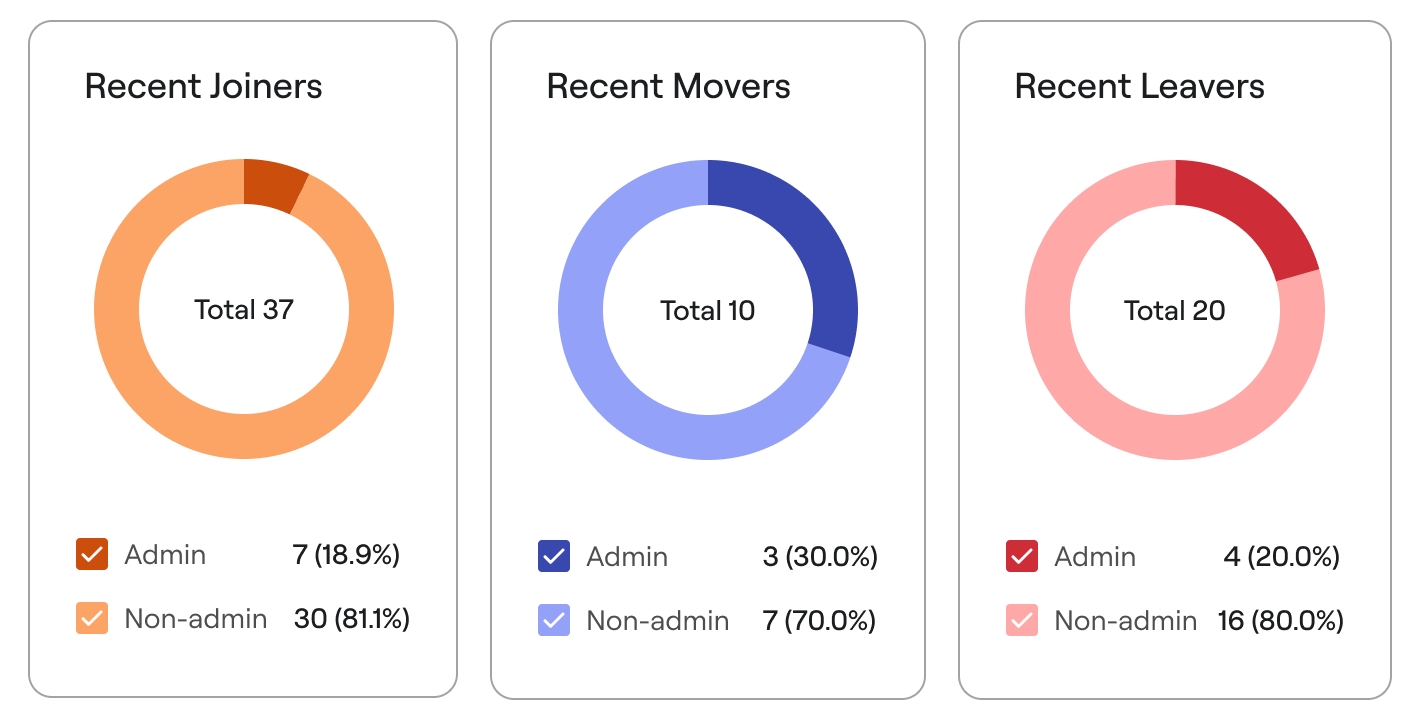
Orchestrate joiner, mover, and leaver scenarios in one place
Manage identity transitions in a single platform, ensuring changes cascade seamlessly across all systems and applications. Axonius enforces policies consistently, eliminates gaps, and reduces operational overhead—so IT teams can swiftly act with confidence and efficiency.
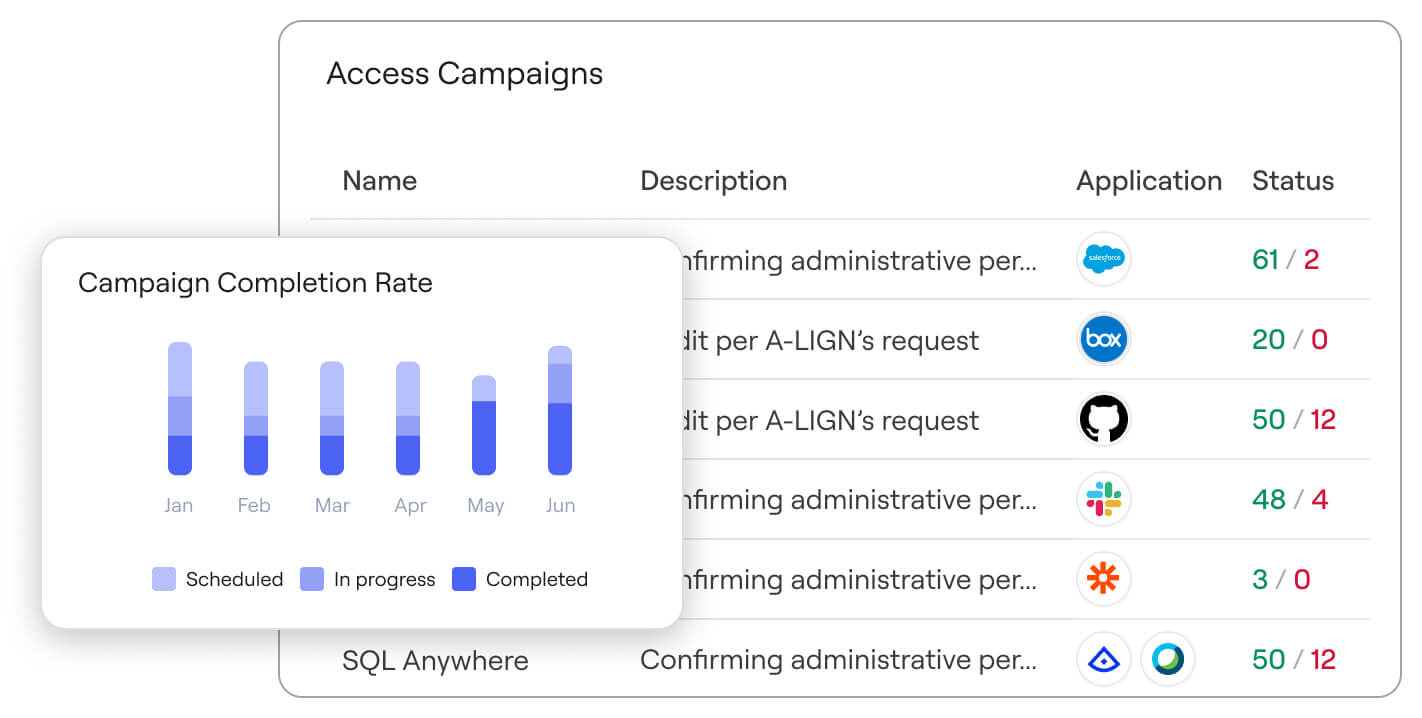
The right way to right-size access
Understand exactly how permissions and entitlements are calculated and granted across all systems. Axonius provides deep insights into access patterns, policy gaps, excessive permissions, and more – enabling teams to intelligently optimize access rights and apply access workflows with confidence.
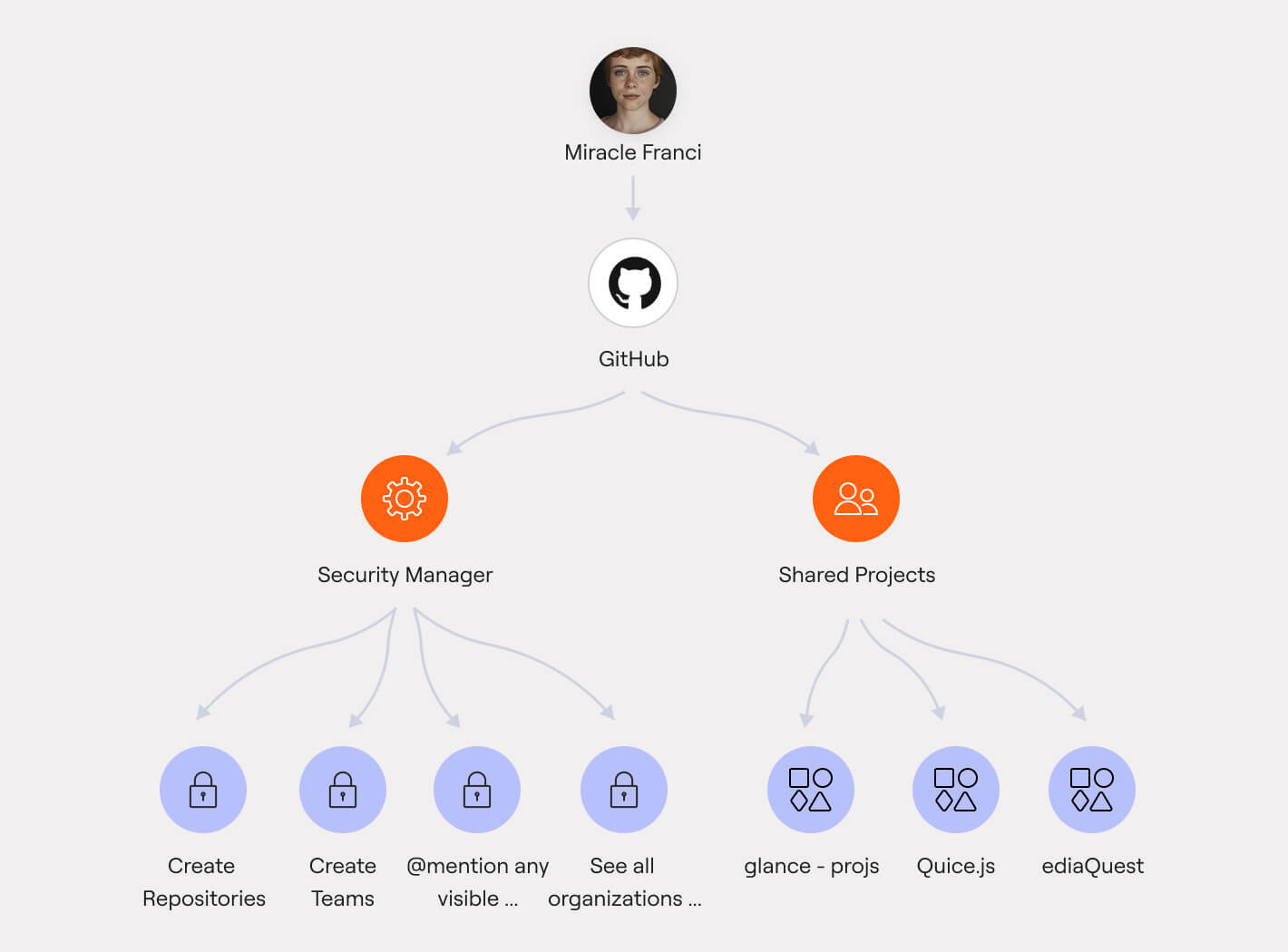
Proactive actions to harden IAM systems
Continuously improve your overall identity security posture with actionable insights into MFA coverage gaps, weak access controls, excessive permissions, policy conflicts, and more to help remediate misconfigurations and exposures before they become exploits.
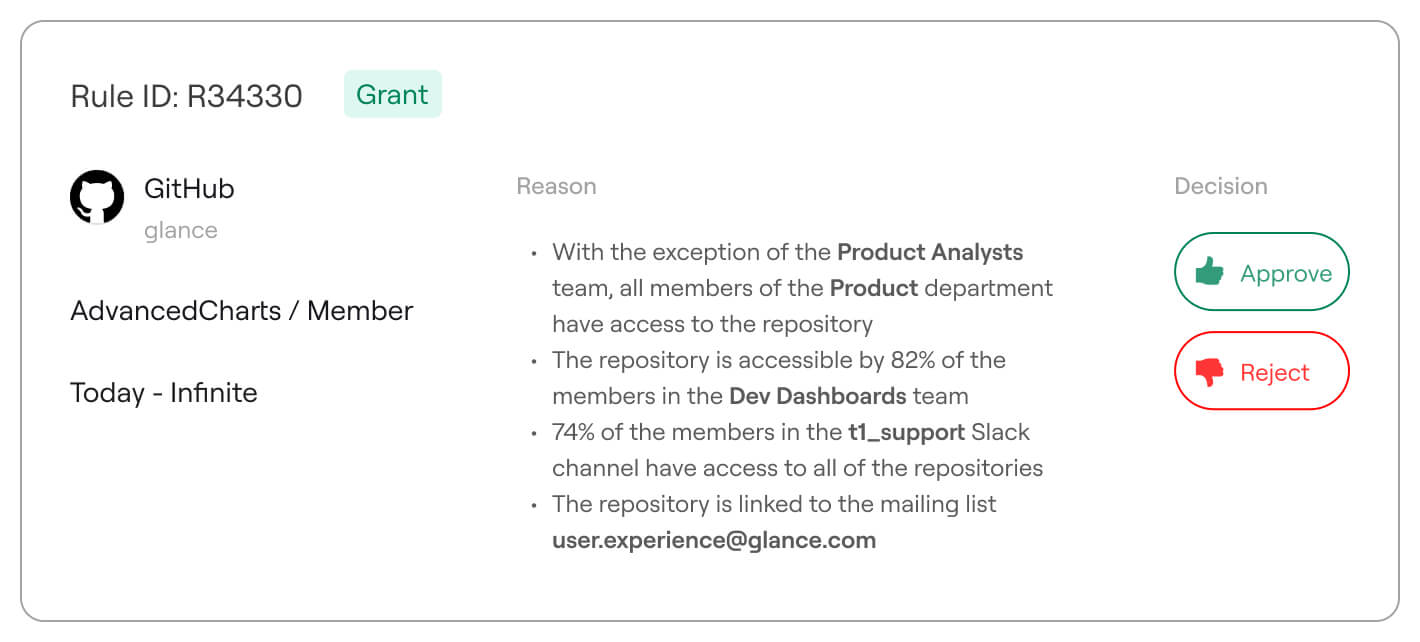
Get clear optimization recommendations
Leverage AI-driven insights to simplify identity policies and enforce least privilege with confidence. Axonius analyzes entitlements, usage patterns, and policy inconsistencies to recommend consolidated rules that eliminate excessive access and streamline governance—helping IT and Security teams maintain a clean, efficient, and resilient identity environment.
Ready to take action across your IAM program?
Schedule a personalized demo with an Axonius specialist.
Axonius brings identity harmony to IT & Security teams

Every identity, all the detail
Axonius aggregates and normalizes identity data across all systems and applications to provide a complete, accurate, and always up-to-date map of your identity fabric.

Hygiene without the hassle
We help you proactively identify and remediate orphaned accounts, excessive permissions, policy drift, and more – keeping identity hygiene clean without the heavy manual lift.

Break the identity silos, not the bank
Axonius brings identity discovery, governance, and security into a single platform without compromising breadth and depth, eliminating silos without costly, complex integrations.

Smarter data-driven decision making
Our identity-centric intelligence analyzes entitlements, usage patterns, and behaviors to uncover hidden risks, optimize access policies, and drive smarter IAM decisions.

The Axonius Asset Cloud
Axonius is where posture, management, and operations converge across your core cybersecurity programs – all backed by our market leading asset intelligence.
See Axonius in action
Discover what’s achievable with a product demo, or talk to an Axonius representative.





.png?width=950&auto=webp&format=jpg&disable=upscale)














