AXONIUS PLATFORM
Cyber Assets
Your trusted system of record for all digital infrastructure to ensure every technology asset across every system is continuously known, compliant, and protected without conflicts or blind spots.
Step up from a static asset inventory to dynamic asset intelligence
Axonius is the market leader in Cyber Asset Attack Surface Management (CAASM) because we integrate with everything, go the extra mile to clean asset data, and enable bi-directional automations to optimize every type of technology asset for compliance, cost, and security posture.
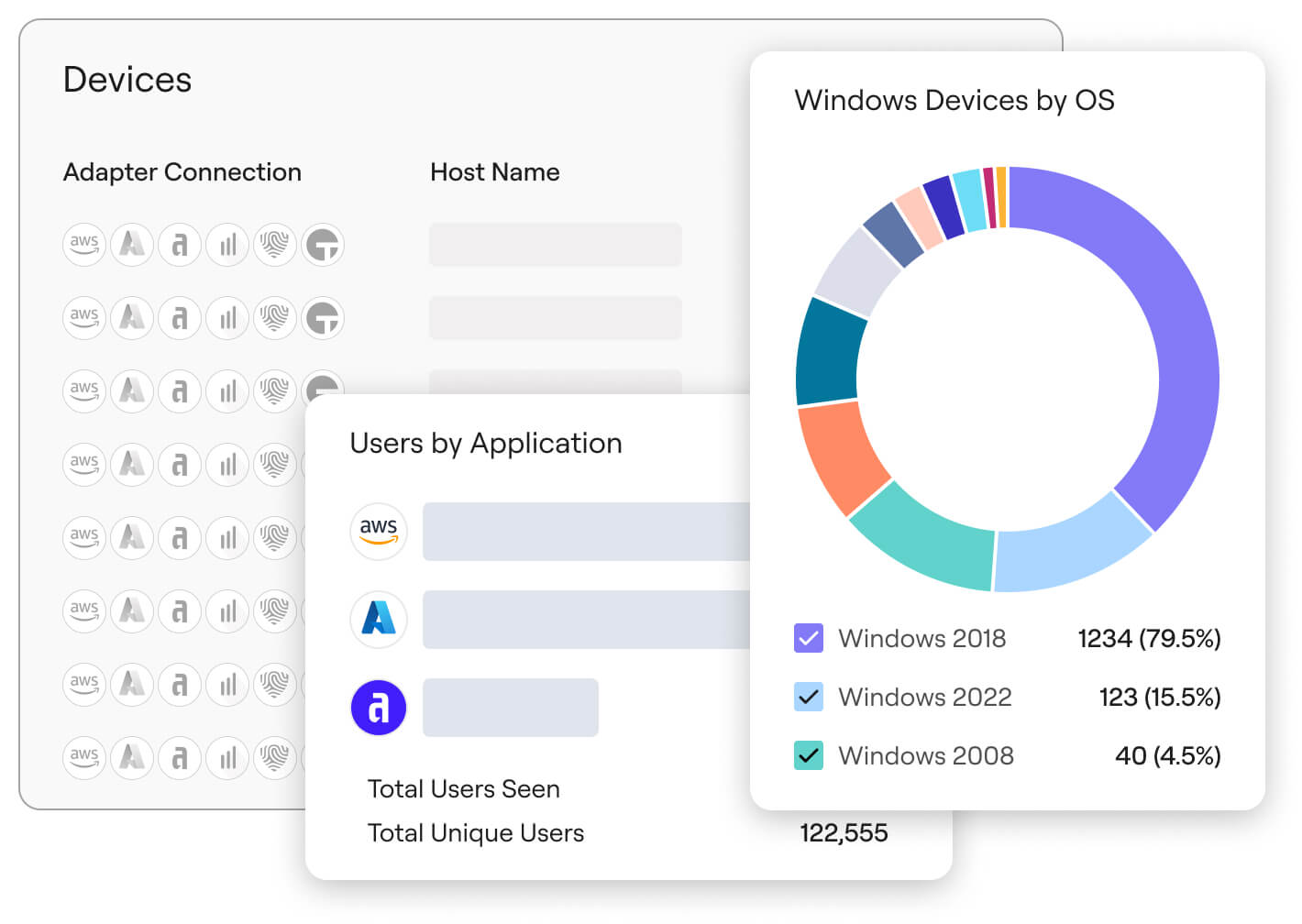
Make actionable sense of your asset data
Ditch the manual spreadsheets and painstaking cross-checking. Axonius does the hard work to continuously normalize, deduplicate, and enrich your aggregated asset data so you always have a complete and accurate picture of your entire technology footprint.
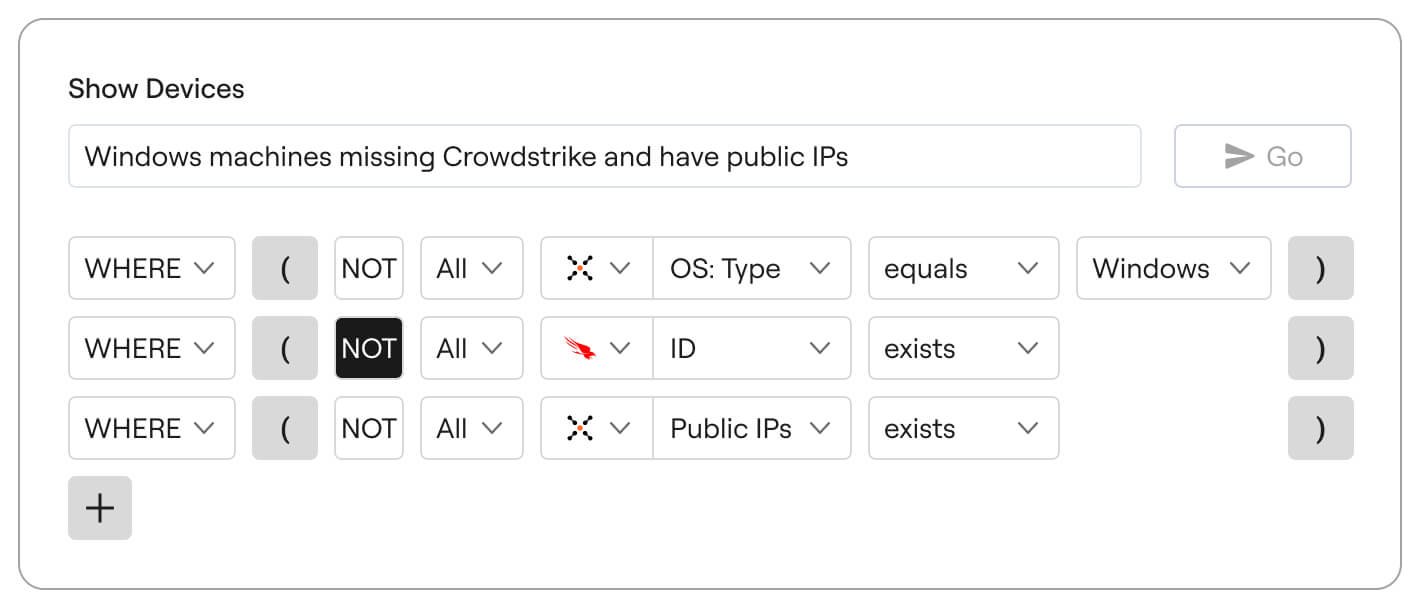
Get blazing fast answers without the guesswork
What do you get with a unified asset data model? A level of visibility like no other. Quickly uncover configuration drift, coverage gaps, weak controls, non-compliant states, and more with a powerful search and discovery toolkit built for accuracy and speed.
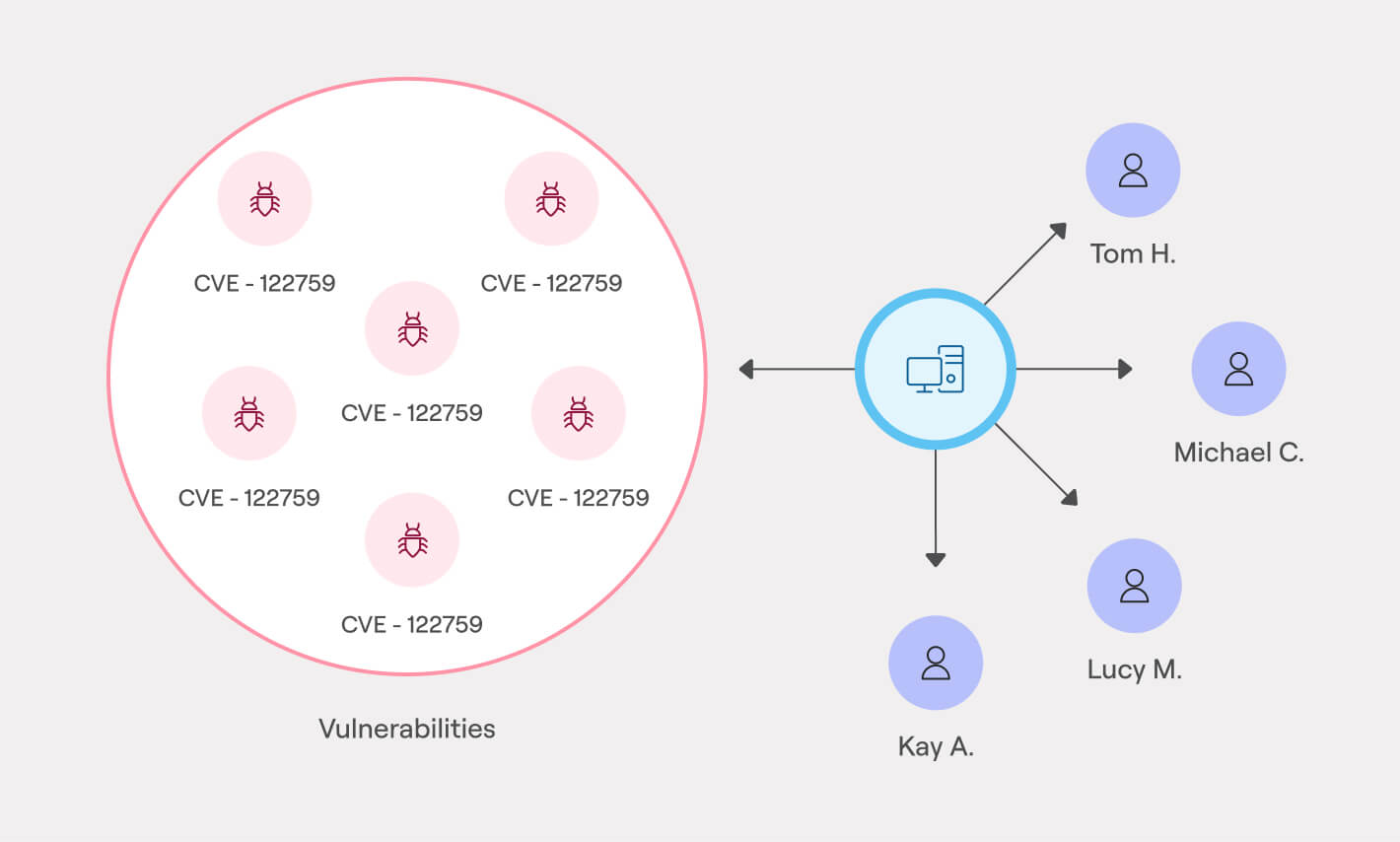
See the whole attack surface, not just the parts
Exposure comes from all angles. Our unique advantage to understanding all assets and their relationships gives you a unique ability to take action with context – whether responding to an incident, optimizing for performance, or hunting for threats.
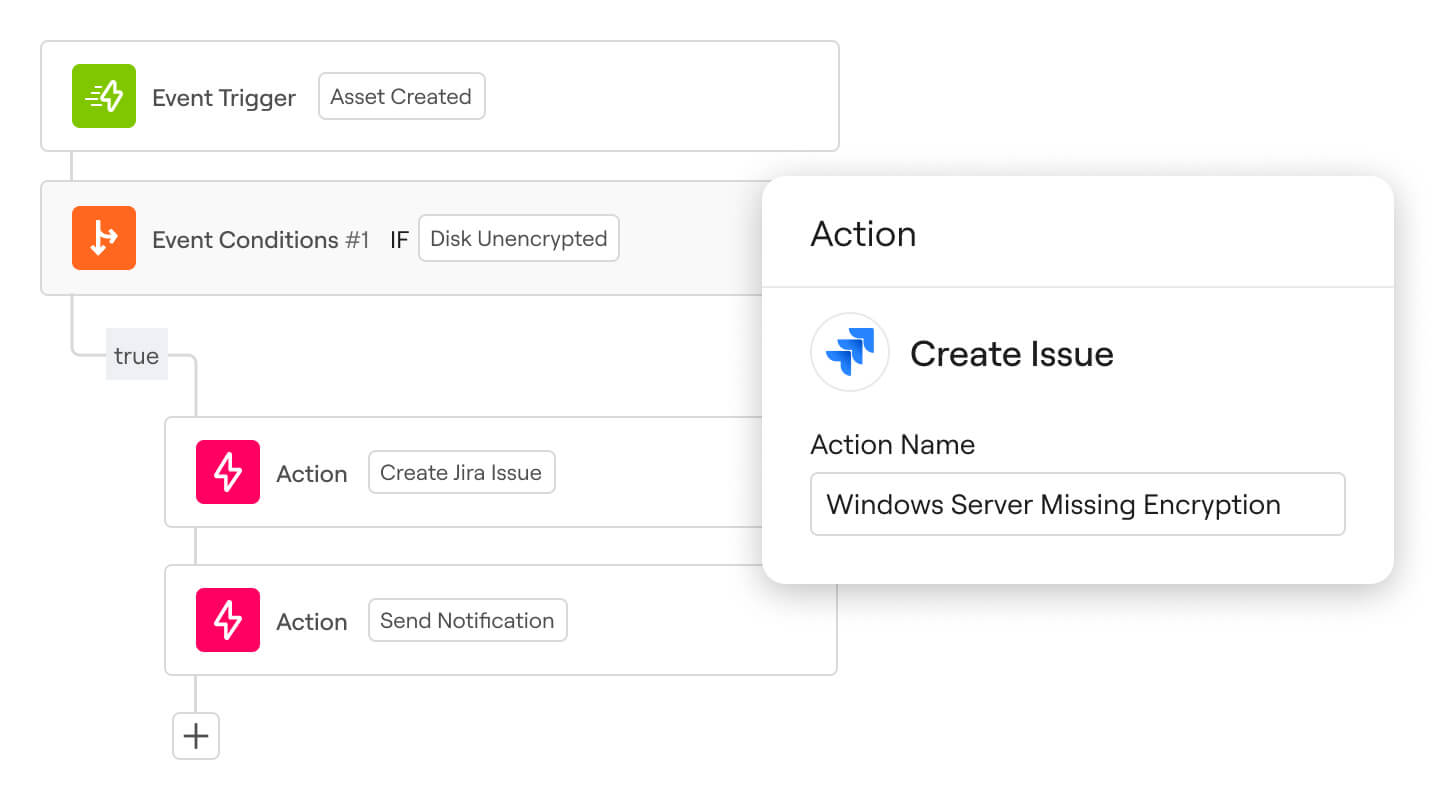
Adhere to security and compliance policies continuously
Your Security & IT Operations don’t stop at visibility. Axonius is purpose-built for action, allowing you to apply controls, enforce policy, fix configurations, remediate vulnerabilities, and more through a centralized toolkit.
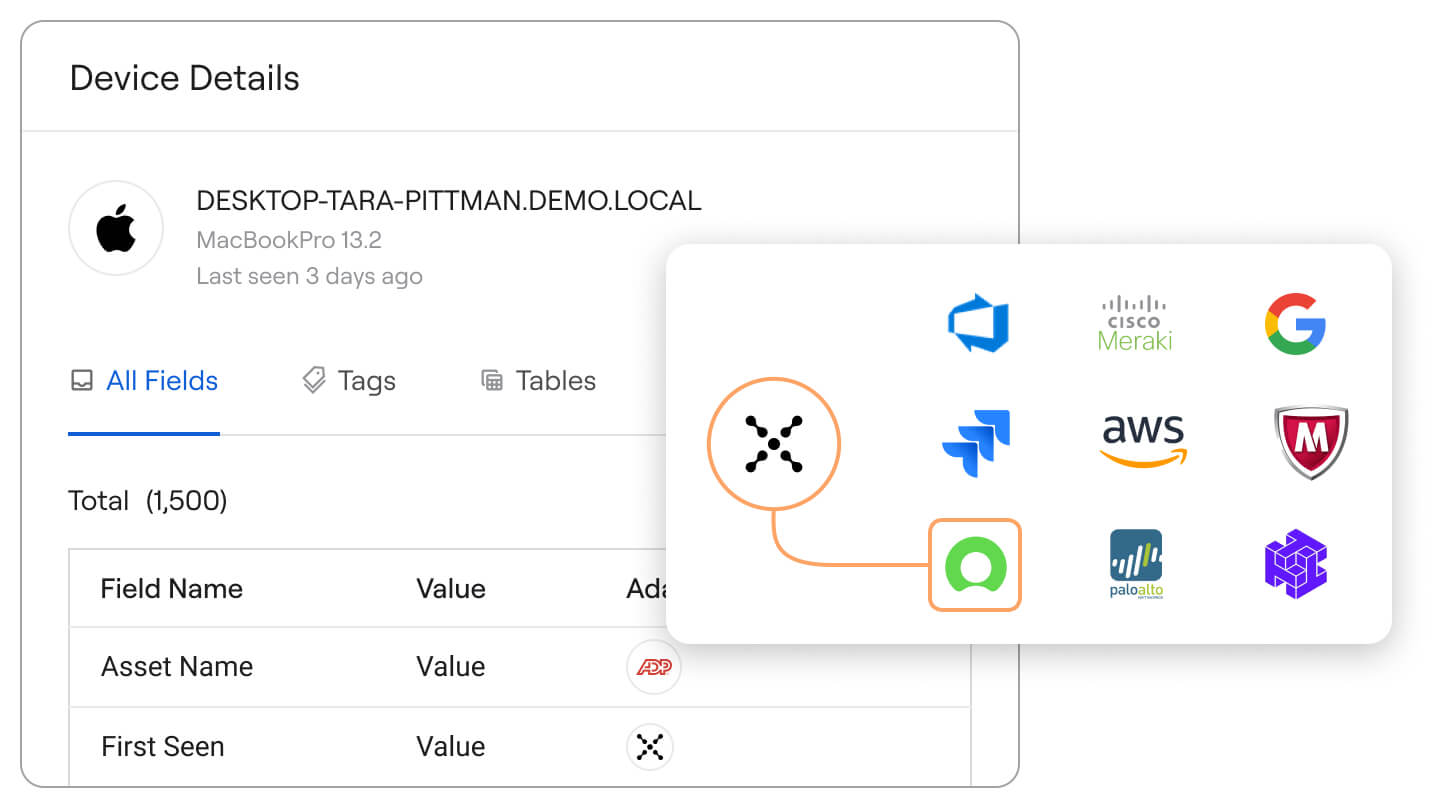
Have all the context wherever you need it
Asset data shows up everywhere – your CMBD, your SIEM, your SOAR, and more. Axonius makes sure every system, every issue, and every report has fully enriched asset data to help you make smart data-driven decisions and prove asset hygiene.
Ready to take action with your cyber asset management?
Schedule a personalized demo with an Axonius specialist.
Axonius is what happens when you don’t compromise on breadth or depth

Always expanding integrations
We’re building out our adapter network every day. With thousands of services and actions available, there are no gaps in your asset data, meaning no blind spots in your attack surface.

Only the cleanest data
It’s a herculean effort to get complete and accurate asset data – we know. Our advanced aggregation pipeline constantly normalizes, deduplicates, and enriches your asset data to the fullest.

Full lifecycle automation
Vulnerabilities surface, configurations drift, and policies fail. With bi-directional integrations across your critical systems, your assets are continuously verified for state, cost, and posture.

Shared platform. Shared language.
Security, IT, and Risk teams have different needs for asset data. Axonius customers leverage the platform to unify assessment, operations, and reporting, breaking down organizational barriers every day.
Customers of all kinds and sizes trust Axonius for Cyber Asset Management

The Axonius Asset Cloud
Axonius is where posture, management, and operations converge across your core cybersecurity programs – all backed by our market leading asset intelligence.
See Axonius in action
Discover what’s achievable with a product demo, or talk to an Axonius representative.




.png?width=950&auto=webp&format=jpg&disable=upscale)



















