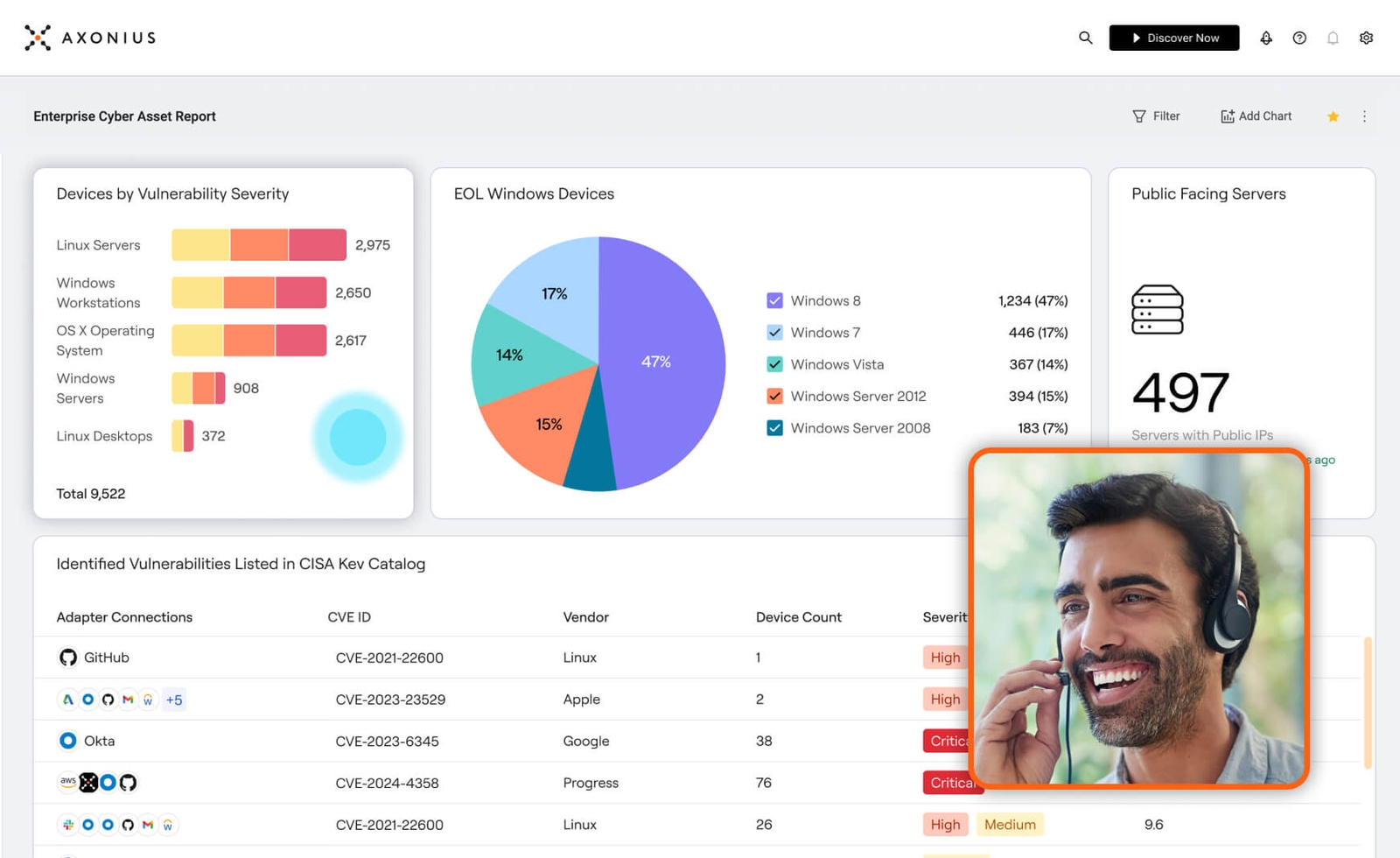
Frameworks and certifications
Axonius uses SOC 2 Trust Services Criteria for Security and ISO 27001 for structuring our security program. These respected frameworks help ensure that we implement comprehensive security measures such as access control, infrastructure and application defenses, risk management, and so on. They also map to other control catalogs, such as those published by NIST and CIS.
These frameworks also provide a way for independent auditors to review our security and communicate it to our customers. To provide such assurance, we obtained an ISO 27001 certificate and the Type 2 SOC 2 attestation from Schellman, an experienced and accredited audit firm. To provide additional assurance to customers that process protected health information, we also obtained a Type 1 attestation for the HIPAA Security Rule and HITECH Breach Notification requirements from Schellman.
Current and prospective Axonius customers can access our SOC 2 and HIPAA reports at the Axonius Trust Center after an NDA is executed with us.




.png?width=950&auto=webp&format=jpg&disable=upscale)