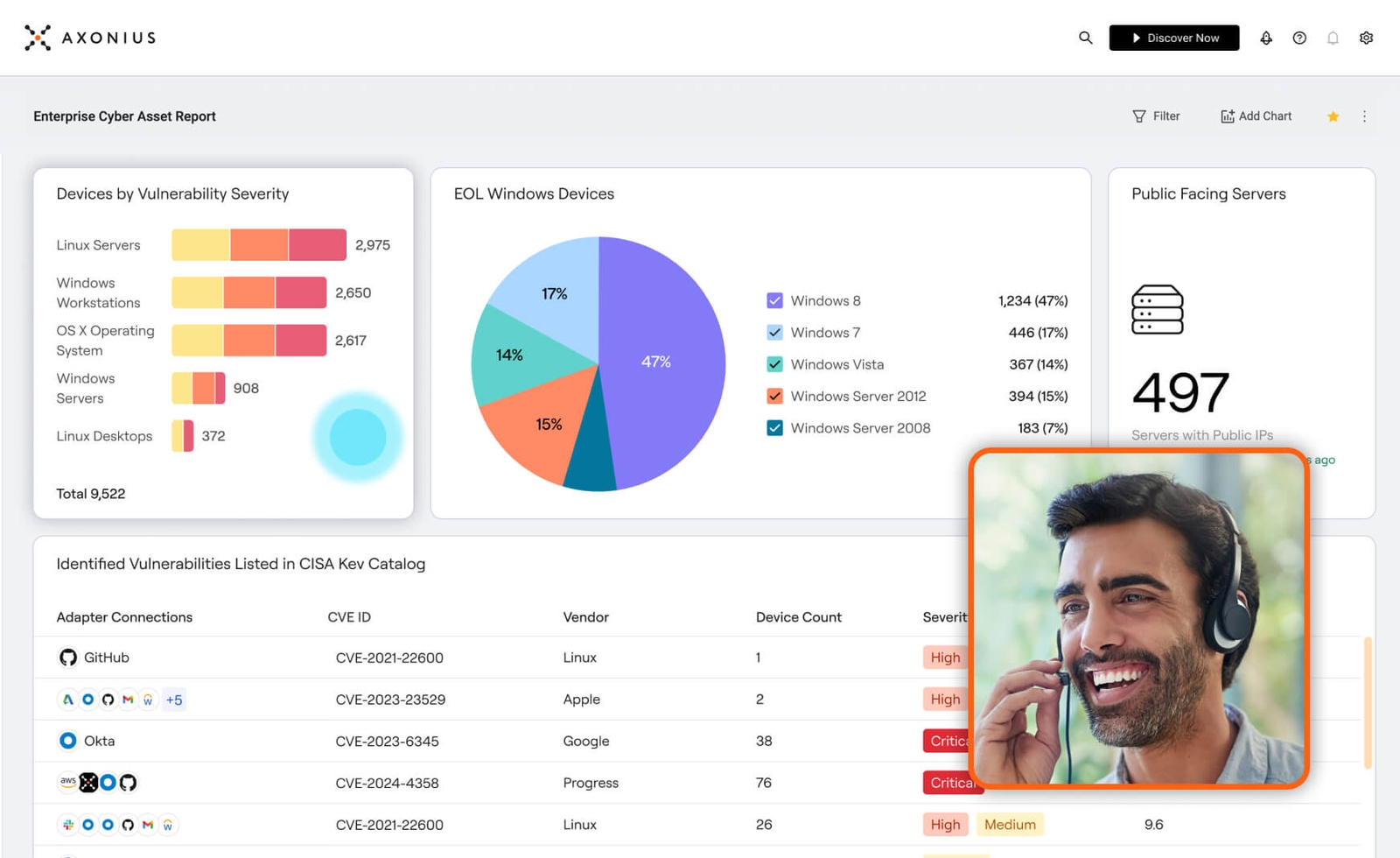
The right answers
We go the extra mile to ensure asset data is complete, accurate, and always up-to-date.

Prioritized for action
Our platform illuminates what’s most important to focus mitigation efforts on what truly matters.

Continuously covered
Every applied control and fix is verified at each turn to ensure policies are consistently upheld.




.png?width=950&auto=webp&format=jpg&disable=upscale)