Bring truth to action with the Axonius Asset Cloud
Preemptively tackle hard-to-spot exposures, misconfigurations, and operational challenges across your entire technology environment — all in one place.
The Axonius Asset Cloud
Security, IT, and GRC teams leverage Axonius to address mission-critical risk, performance, and cost measures across their enterprise.
- Cyber Assets
- Software Assets
- SaaS Applications
- Exposures
- Identities
Cyber Assets
Continuously minimize your attack surface
Your trusted system of record for all digital infrastructure to ensure every technology asset across every system is continuously known, compliant, and protected without conflicts or blind spots.
Track agent coverage
Map asset compliance
Reconcile CMDB inventory
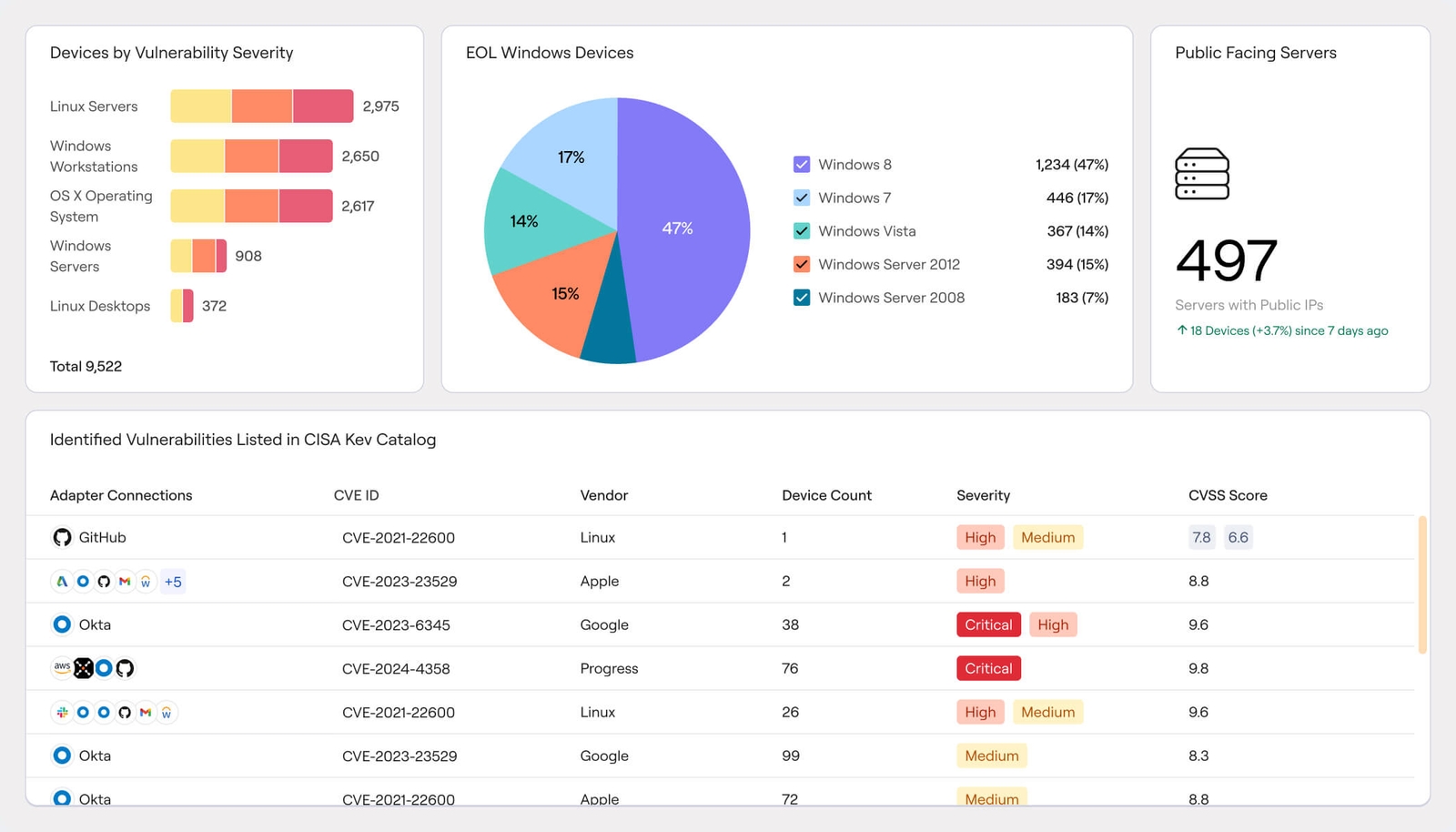
Software Assets
Manage software lifecycles, risk, and spend
Comprehensive, actionable visibility into software usage across the organization – empowering Security, IT, and GRC teams to uncover unsanctioned software, manage EOL/EOS, remediate vulnerabilities, and take control of costs.
Manage unified software catalog
Automate removal campaigns
Automate software updates

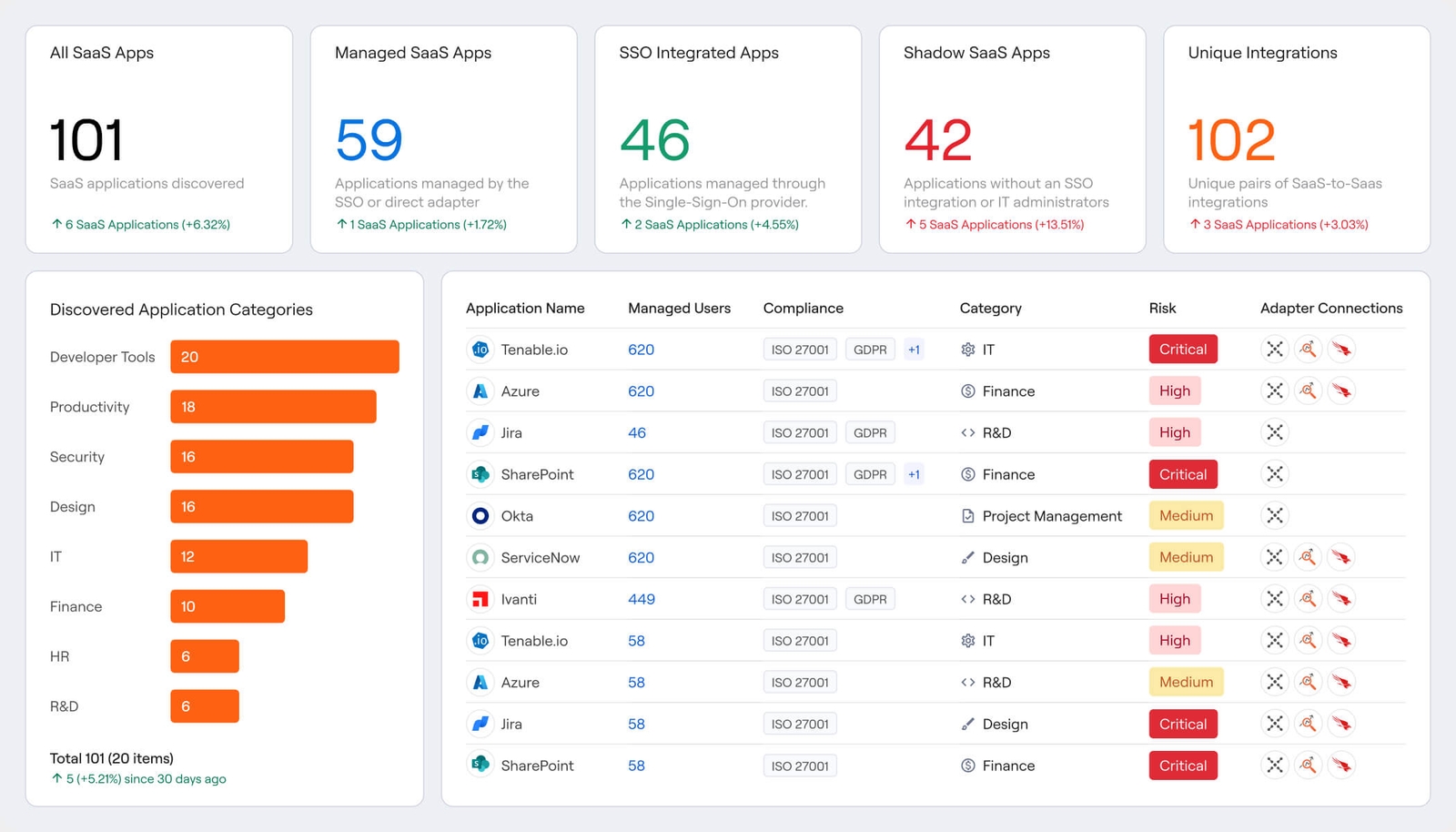
SaaS Applications
Manage application lifecycles, risk, and spend
Get total coverage across your entire SaaS landscape to build a complete inventory, mitigate critical risk areas, and optimize usage & spend in one place.
Reconcile unsanctioned apps
Mitigate misconfigured settings
Optimize SaaS spend
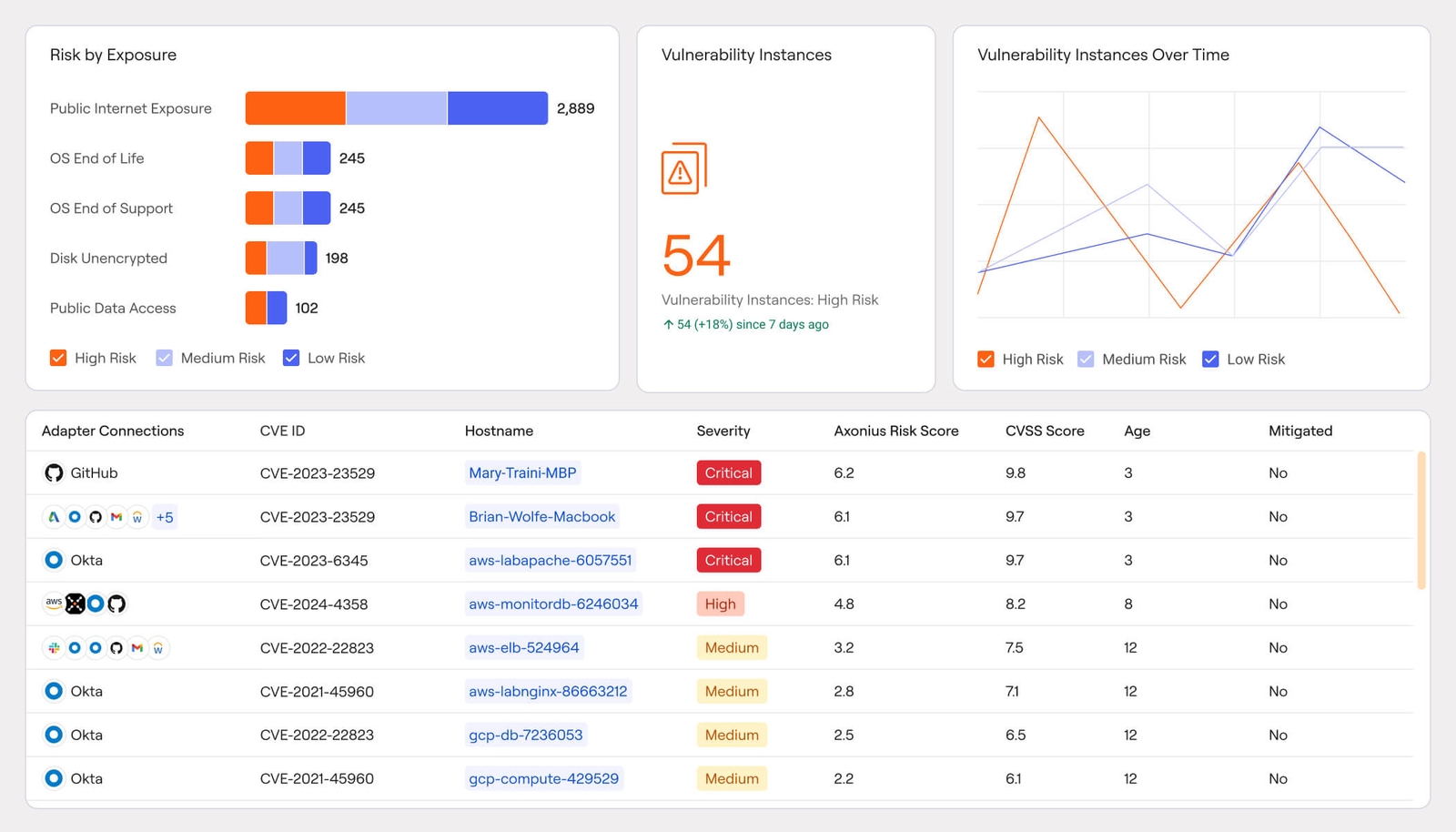
Exposures
Get precisely proactive with your mitigation efforts
Put your proactive cybersecurity measures in the driver's seat with a single place to unify exposure findings, correlate and rank risks, and execute prioritized large-scale mitigation efforts.
Consolidate vulnerability management
Define risk scoring & prioritization measures
Automate patching workflows
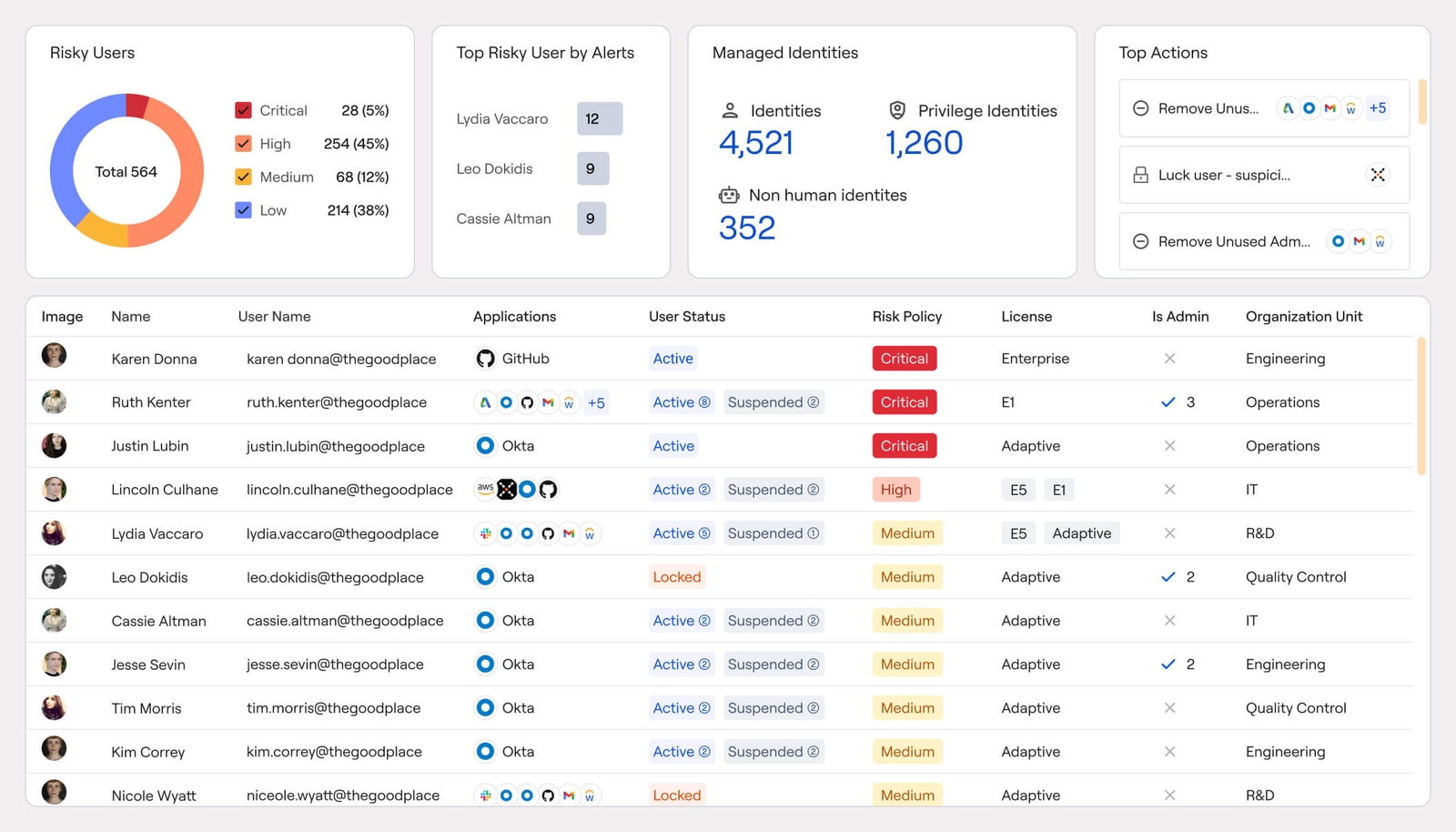
Identities
Unify IAM program management and security
Unify all identity artifacts in one place to transform fragmented data into actionable insights – centralizing discovery, governance, posture, and incident response efforts for your IAM programs.
Automate JML lifecycle actions
Run access certification campaigns
Optimize role mining & permissions

Gain total attack surface awareness in a single view
Axonius brings clarity to chaos by unifying scattered asset data into a complete, accurate, and up-to-date view—so you can pinpoint risks, close coverage gaps, and act with confidence.
Axonius provides us with a single source of visibility and a single source of truth.


Elevate security and hygiene insights that deserve attention
Our platform surfaces the insights that truly matter—bringing risk, performance, and cost into focus while delivering clear recommendations to drive impactful action.
Axonius took what we thought we knew about our assets and gave us something a lot closer to the truth.


Get laser sharp with running critical fixes at scale
We help you zero in on the most critical opportunities, empowering teams to scale mitigation efforts efficiently—always aligned with their capacity and priorities.
We have a better understanding of ‘what’s out there’ than ever before, and can take proactive steps to mitigate any issues, vulnerabilities, or problems.


Ensure direct, continuous policy enforcement across systems
Take the guesswork out of policy adherence, ensuring every asset stays aligned with your requirements through continuous monitoring and automatic enforcement.
We can automate more tasks because we have a source of truth that can tell us if something's net new, if something's out of compliance, if something's in a state that's not what we consider normal.


Manage asset coverage from end-to-end across programs
Let us help lighten the load for your critical cybersecurity programs, tracking everything from maturity to KPIs, so you can report with confidence and focus on what matters most.
Axonius provides the luxury of being able to evaluate where we stand by quickly visualizing our gaps as we build out our cybersecurity program.

See Axonius in action
Discover what’s achievable with a product demo, or talk to an Axonius representative.























