How to Track and Report Cybersecurity Metrics with Axonius
Axonius

If you had to prove the value of your cybersecurity program to your organization right now—could you do it?
Could you confidently pull the right metrics? Or is your data scattered across tools, hard to interpret, or missing key context?
If you’re struggling to meet the demand for key performance indicators (KPIs), key risk indicators (KRIs), and key control indicators (KCIs)—and translate metrics into terms that matter to the business—you’re not alone.
We’ll walk through how to report on your systems and demonstrate your cybersecurity program’s impact on risk management. Let’s dig into a practical approach to tracking, measuring, and acting on security data with Axonius.
Watch James Flores break down how to track and report cybersecurity metrics. Keep reading for a step-by-step guide.
1. Build a Solid Security Baseline
What You Need to Succeed
Before you can take meaningful cybersecurity metrics, you need a solid foundation—a baseline that accounts for all assets interacting with your data and processes, no matter what they are. This includes everything from devices to identities, installed software to SaaS applications, and assets hosted on-prem, in public clouds, or private clouds.
Think of it like personal finance: if you don’t account for all your debt, your financial picture might seem great, but it’s not accurate. The same applies to cybersecurity metrics.
If you don’t have complete visibility into your assets—devices, users, cloud instances, applications, security controls—you’re operating on incomplete data.
Here’s How to Do It
Get total asset visibility. Axonius’s API-based integrations pull in data from all your security tools, so your inventory reflects every device, user, and cloud instance.
Uncover security blind spots. Automatically correlate data across tools, detect inconsistencies, and surface shadow assets.
Validate your cybersecurity posture from day one. No more guessing if a device is unmanaged or a control is missing.
Cybersecurity metrics are only as valuable as the data behind them. That’s part of why security leaders find Axonius transformative:
“The sheer excitement my team feels to have visibility into what’s in our environment and to have it all in one location—I can’t express how important that is for us.”
– James Loomis, CISO, Mindbody
See how Mindbody eliminated blind spots and built a complete asset inventory with Axonius
2. Visualize and Report on Cybersecurity Metrics
What You Need to Succeed
Once you have a clear security baseline, the next step is turning data into meaningful insights. But for many security teams, security data is scattered across too many tools, making it hard to see the full picture (a reality you might already know all too well).
To effectively track and communicate cybersecurity’s impact, you need a way to instantly visualize your cybersecurity posture and generate reports without time-consuming manual effort.
Here’s How to Do It
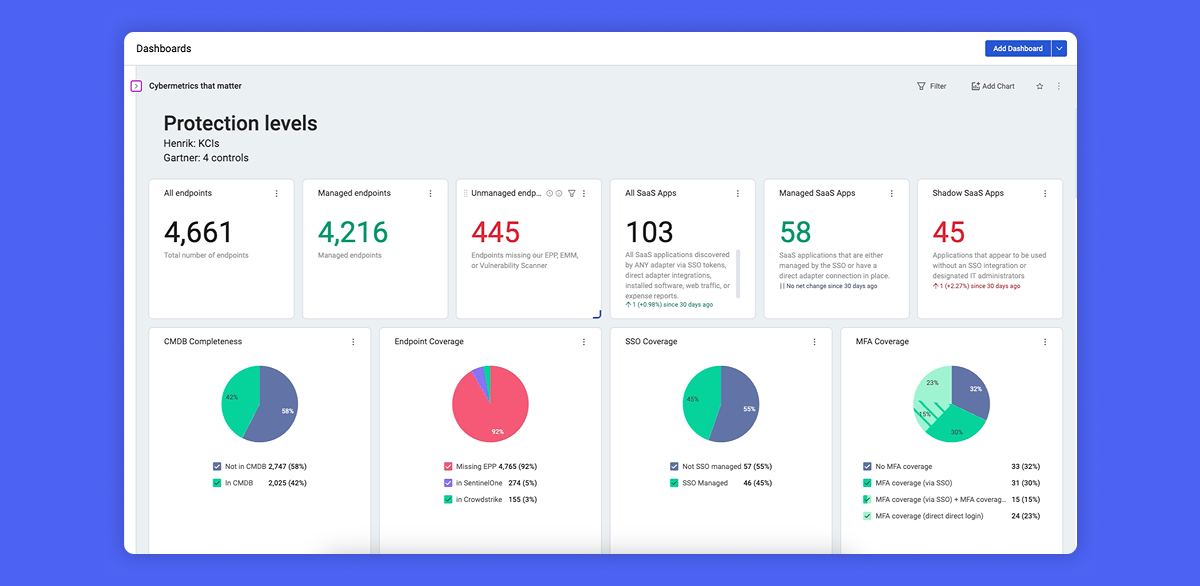
See everything in one place. The Axonius dashboard unifies data from all your security tools, giving you an instant, real-time view of your security posture.
Turn data into actionable insights. Use automated dashboards to track KPIs, KRIs, and KCIs without manual data pulls.
Get executive-ready insights. Axonius makes it easy to translate technical metrics into business-friendly cybersecurity reporting.
3. Take Action on Security Insights
What You Need to Succeed
Metrics aren’t truly valuable if they just sit on a dashboard. Their real value comes from turning insights into tangible cybersecurity improvements and outcomes.
But many teams get stuck in reaction mode—identifying problems from the data, yet lacking the time or resources to act quickly. (Sound familiar?)
You need a way to automate responses to security gaps and enforce policies consistently across all assets. And in the long run, you need continuous monitoring to adapt to new threats as they emerge.
Here’s How to Do It
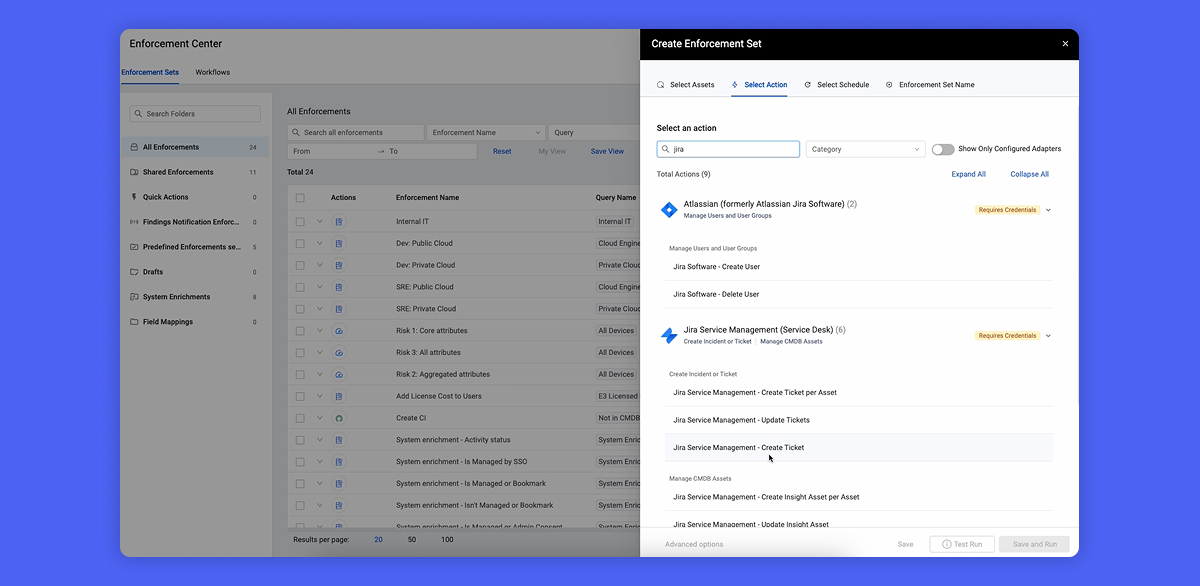
Fix gaps the moment they appear. Axonius lets you surface risks, like unmanaged devices or missing security controls, in real time.
Automate security enforcement. No more reactive firefighting. Set automated actions to deploy security agents, open tickets, or notify teams the moment an issue arises.
Stay ahead of threats without manual effort. Axonius enforcement policies run continuously, so you can detect and resolve risks automatically—before they become bigger problems.
Tracking and Acting on Cybersecurity Metrics Shouldn’t Be Complicated
You and your team have enough to manage—tracking and reporting on security performance shouldn’t be another burden.
With a strong baseline, consolidated insights, and the ability to take action, you can finally get ahead of the curve. No more manual data pulls. No more uncertainty. Just clear, actionable intelligence that drives real security outcomes.
Get a product demo or speak with a representative today and learn how Axonius can help you:
Gain total attack surface awareness in a single view.
Elevate security and hygiene insights that deserve attention.
Run critical fixes at scale with laser-sharp precision.
Ensure direct, continuous policy enforcement across systems.
Manage asset coverage from end to end across programs.
Categories
- Asset Management
Get Started
Discover what’s achievable with a product demo, or talk to an Axonius representative.




.png?width=950&auto=webp&format=jpg&disable=upscale)