The Right Way to Build a Metrics-Driven Cybersecurity Program
Axonius

Is your cybersecurity program “working”?
If you haven’t suffered a breach, your answer might be, “I guess so.” But the absence of a breach isn’t enough to reveal whether you're doing well or are just a sitting duck.
Security leaders must move past one-off anecdotes. Instead, they need structured, outcome-driven metrics that provide a clear picture of cybersecurity performance while aligning with business goals and corporate security investments.
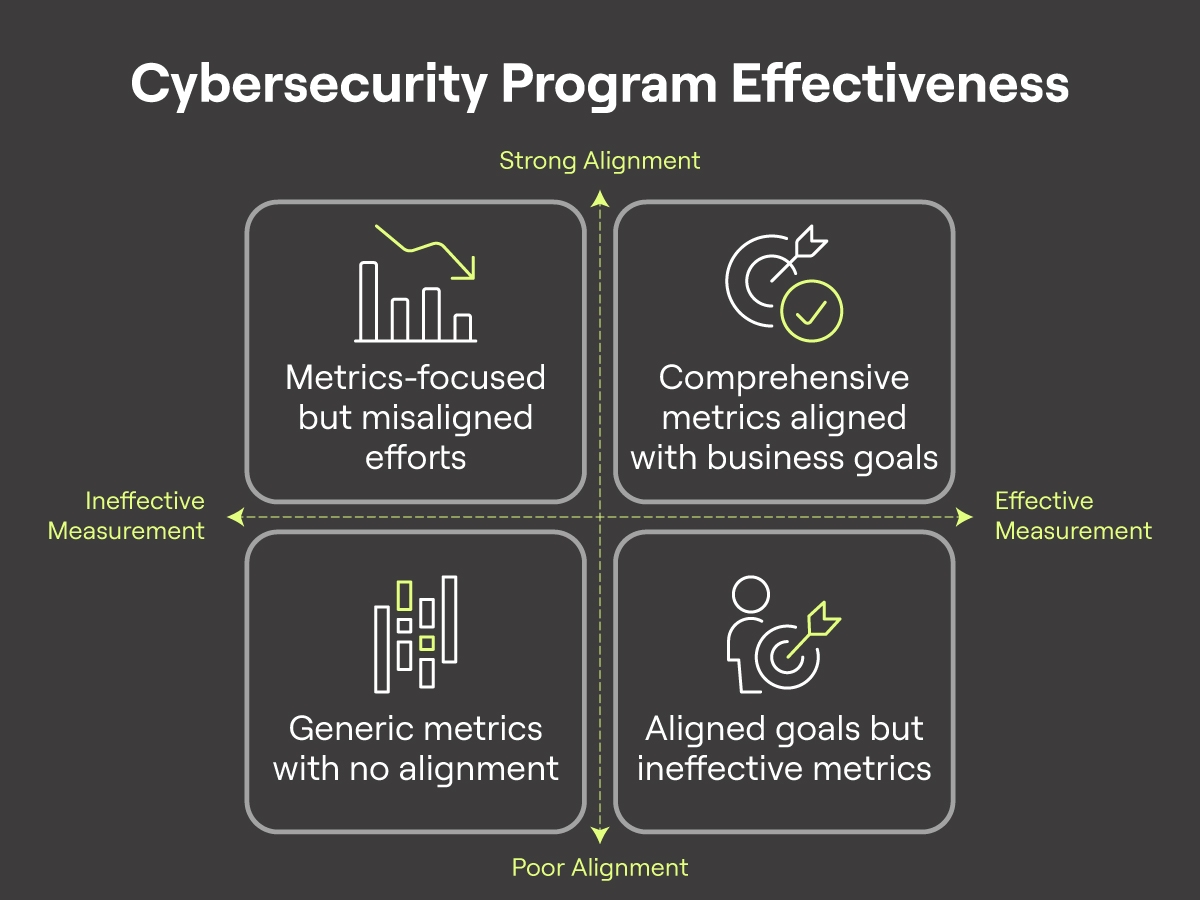
The key is to measure outcomes, track trends over time, and contextualize metrics to organizational objectives—demonstrating how cyber asset security drives business success.
We’ll show you how. Here’s our guide to building a metrics-driven cybersecurity program.
But First: Get Comfortable with the Three Types of Cybersecurity Metrics

Key Performance Indicators (KPIs)
KPIs track progress toward strategic security goals and demonstrate how security initiatives support business objectives.
Examples of KPIs
- Security spending governance
- $ saved from blocked incidents
- % of employees trained on security awareness
- Average SLA times for security response
Key Risk Indicators (KRIs)
KRIs signal the potential risks to the business, helping teams identify vulnerabilities and prevent breaches before they happen.
Examples of KRIs
- Quarterly or semi-annual pass rate for audits
- # of security incidents or data breaches
- % of business units that fail to adhere to organizational security policies
- Vulnerabilities identified vs. vulnerabilities patched in a given month or quarter
Key Control Indicators (KCIs)
KCIs assess the effectiveness of your organization’s security policies, processes, and systems. You’ll get the best sense of the effectiveness of your security program if you’re able to examine historical trends in KCIs that are contextualized to your actual security and business initiatives.
Examples of KCIs
- % of assets in policy
- Mean time to detect
- Mean time to recover
- % of incidents with critical business impact
- % of critical assets covered by vulnerability scanning
How to Build A Cybersecurity Metrics Framework
Now it’s time to quantify your success. Follow these five steps to build a meaningful cybersecurity metrics framework:
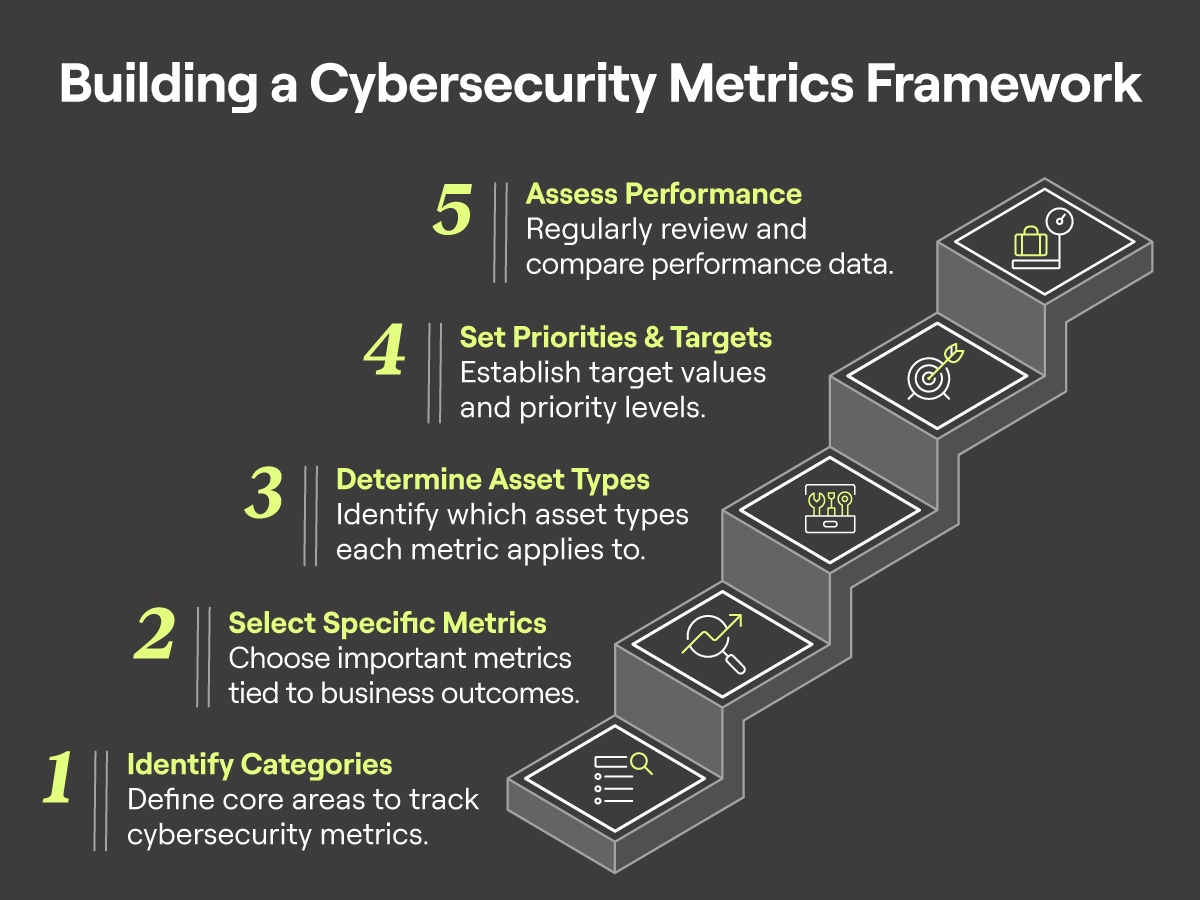
- Identify Your Metric Categories
Start by identifying the core areas your metrics will track. Common categories include asset discovery, identity management, and vulnerability management. - Identify Specific Metrics Within Each Category
Leaders care most about metrics tied to business outcomes, such as how fast incidents are contained, how well systems are patched, and how effective employee training is. - Determine Your Asset Types for Each Metric
Identify which asset type each metric applies to. For example, endpoints, infrastructure, applications, and users. - Set Priorities and Targets
For each metric, define a target value and establish priority levels to drive focus where it matters most. - Compare Performance and Assess Your Position
Review the data for each metric and see how it compares to your targets. Ask yourself: Am I making progress at a reasonable pace? Is my organization at risk and in need of improvement?
Tip: In Cybersecurity Metrics for Dummies, we dive more into frameworks and what/how to measure.
Simplifying Metrics Complexity with the Right Tools
Increasing IT complexity has created a headache for security teams. User devices, identities, applications, cloud infrastructure, critical systems…the list goes on. This flood of solutions amounts to an overwhelming volume of reports and metrics—many of which teams lack the time or expertise to act on effectively.
The goal is to have just one tool that gives you a single, comprehensive view of your assets and risk. Axonius unifies data across all assets, providing a single source of truth to track key security metrics.
By identifying vulnerabilities, prioritizing fixes, and automating security enforcement, Axonius helps your team:
- Reduce time spent collecting and analyzing asset data
- Improve security coverage across critical assets
- Optimize cybersecurity investments with measurable outcomes
Read Cybersecurity Metrics for Dummies
For a deeper dive into how to structure and optimize your cybersecurity metrics, download Cybersecurity Metrics for Dummies.
You’ll learn how to:
- Understand your total attack surface and uncover security gaps
- Identify outcome-driven metrics that will be meaningful to your board
- Take action on your cybersecurity metrics findings to keep your business safe

Categories
- Asset Management
Get Started
Discover what’s achievable with a product demo, or talk to an Axonius representative.





.png?width=950&auto=webp&format=jpg&disable=upscale)