2025 Cybersecurity Trends (And How They’ll Impact You)
Axonius

Between generative AI, expanding attack surfaces, and the explosion of machine identities, security and risk management (SRM) leaders face a demanding year ahead. In these uncertain times, cybersecurity teams need clarity on where to direct their efforts—and the latest insights from Gartner® Top Trends in Cybersecurity for 2025 offer a clear roadmap for what's on the horizon.
What’s really driving cybersecurity this year? It all comes down to closing critical visibility gaps, dismantling silos, and making smart, data-driven decisions.
Let’s break down what we found most compelling from the Gartner findings and explore what they mean for your team.
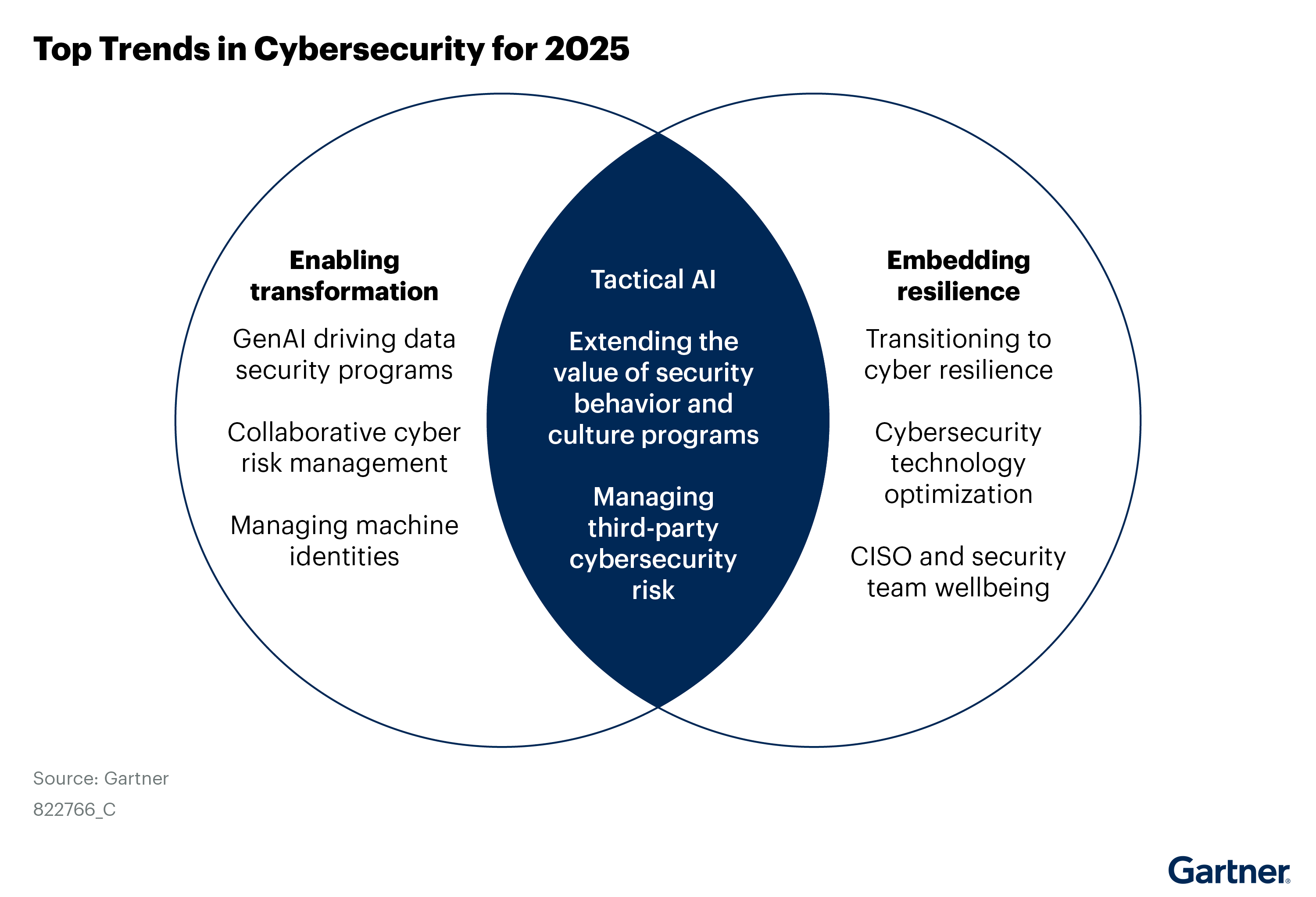
Source: Gartner, Top Trends in Cybersecurity for 2025, Richard Addiscott, Anson Chen, Joerg Fritsch, Tom Scholtz, Will Candrick, Jeremy D'Hoinne, John Watts, Chiara Girardi, Manuel Acosta, Felix Gaehtgens, Oscar Isaka, Alex Michaels, 12 December 2024.
Trend 1: Cyber Resilience Is Non-Negotiable—Boards Are Paying Attention
What to expect: Cybersecurity is no longer just IT’s problem—it has evolved into a strategic asset that’s integral to every business operation.
“84% of board directors view cybersecurity as a business risk, up from just over half in 2016” (Top Trends in Cybersecurity for 2025, p. 13).
Transitioning to a resilience mindset means adopting adaptive strategies that not only prevent threats but also ensure rapid recovery. Leaders are now expected to focus on safeguarding revenue streams, minimizing operational downtime, and reinforcing customer trust.
The bottom line: Cybersecurity’s true value is realized when emerging threats are turned into opportunities for building a robust, agile defense, ensuring the organization remains both secure and competitive.
Trend 2: Cyber Risk Management Is Evolving—Collaboration Is Vital
What to expect: As technology decisions increasingly shift to business technologists, traditional centralized cyber-risk management is being outpaced by evolving business needs.
Today, effective risk management relies on a collaborative model where decision-making is decentralized, empowering risk owners to act swiftly while still accounting for enterprise-wide impacts. This integrated approach not only enhances agility but also nurtures a culture of shared accountability and continuous improvement.
The bottom line: Fragmented workflows make it difficult to comprehensively manage risk. By unifying visibility, standardizing processes, and embedding accountability across the organization, teams can make informed decisions that proactively mitigate risk and align with broader business priorities.
Trend 3: Tech Stacks Are Expanding—Smarter Optimization Is Essential
What to expect: Security teams need smarter ways to optimize their existing tools. Balancing platform consolidation with the flexibility of specialized point solutions, while leveraging a cybersecurity mesh architecture, can streamline processes and reduce operational complexity.
“The average organization has 43 tools in its cybersecurity product portfolio, and 5% of organizations have more than 100 tools” (Top Trends in Cybersecurity for 2025, p. 16).
The bottom line: Simplification and integration are key. Evaluating your technology portfolio to eliminate redundancies and enhance interoperability not only improves efficiency but also strengthens your organization’s overall agility and threat response capabilities.
Trend 4: Generative AI Is Reshaping Data Security—Context Is King
What to expect: Generative AI is redefining data security programs by rapidly processing mountains of information, uncovering hidden anomalies you might not spot manually.
However, its power is inherently tied to the quality of the data it analyzes. Poor or incomplete data can result in misleading insights, undermining the benefits of AI-driven security.
The bottom line: AI isn’t magic; you need to feed it clean, accurate data. Invest in synthetic data tools, establish robust data governance, and secure unstructured data. This ensures that generative AI delivers actionable intelligence rather than generating distracting false positives.
Trend 5: Machine Identities Are Growing—And So Are the Risks
What to expect: While AI grabs the headlines, machine identities (like APIs, certificates, and service accounts) are quietly becoming one of the biggest challenges in cybersecurity. These digital identities, which now outnumber human ones, are increasingly exploited by attackers if not managed effectively.
Organizations must integrate machine identity management into their overall security strategy, extending existing IAM frameworks to cover every digital entity. This approach involves dynamic monitoring, automated remediation, and continuous risk assessment to prevent lateral movement by threat actors.
The bottom line: You wouldn’t ignore user identity management—don’t skip it for machines. Every API, key, and certificate is a potential security gap if you’re not paying attention. A robust strategy for machine identity management is essential to protecting your organization’s growing digital footprint.
What’s Next? The Biggest Risks to Watch
Even with all the right tools and strategies, some risks keep surfacing:
- Automation Without a Trusted Foundation: Automation is helpful, but it’s not foolproof. It must be supported by reliable, data-driven intelligence to correctly identify and manage nuanced threats.
- Fragmented Visibility: Siloed tools create blind spots, making it hard to detect and act on threats effectively. This has held many teams back from centralizing and automating processes.
- Weak Foundations for New Tech: AI, IoT, and other innovations bring new vulnerabilities if security fundamentals aren’t solid. This will continue to be an evolving area.
What Cybersecurity Leaders Should Focus On
To tackle these trends and challenges, organizations should focus on three key areas:
- Get a Single Source of Truth: Establish unified asset visibility as the foundation for effective security, ensuring that every action is informed by accurate data.
- Integrate Your Tools: Break down silos to create streamlined workflows and reduce errors.
- Align Security with Business Goals: Demonstrate how security initiatives drive revenue, reduce downtime, and enhance customer trust.
Cybersecurity in 2025—Turning Trends into Opportunities
For cybersecurity, 2025 isn’t about doing more—it’s about doing it smarter. With the right strategies, tools, and mindset, you can move beyond reactive security to proactive, business-aligned solutions. Access Gartner complimentary research to build a strategy that makes an impact this year.
Categories
- Asset Management
Get Started
Discover what’s achievable with a product demo, or talk to an Axonius representative.







