Axonius recently hosted The Great Debate, a 10-part webinar series debating the merits and pitfalls of some of the hottest topics in cybersecurity today. This blog post recaps the key takeaways from the first episode, where our guest speakers argued the pros and cons of prioritizing Zero Trust.
Read on to find out whether Zero Trust should be the No. 1 cybersecurity initiative for IT and security professionals in 2021.
What is Zero Trust?
Coined in 2010 by former Forrester analyst John Kindervag, Zero Trust is a security model that advocates moving security away from a perimeter-centric approach and instead adopting a model that relies on continuous verification of trust across every device, user, and application. It does this by pivoting away from the trust but verify approach to a never trust and always verify approach.
In practice, this model considers all resources to be external. It continuously verifies trust before granting only the required access.
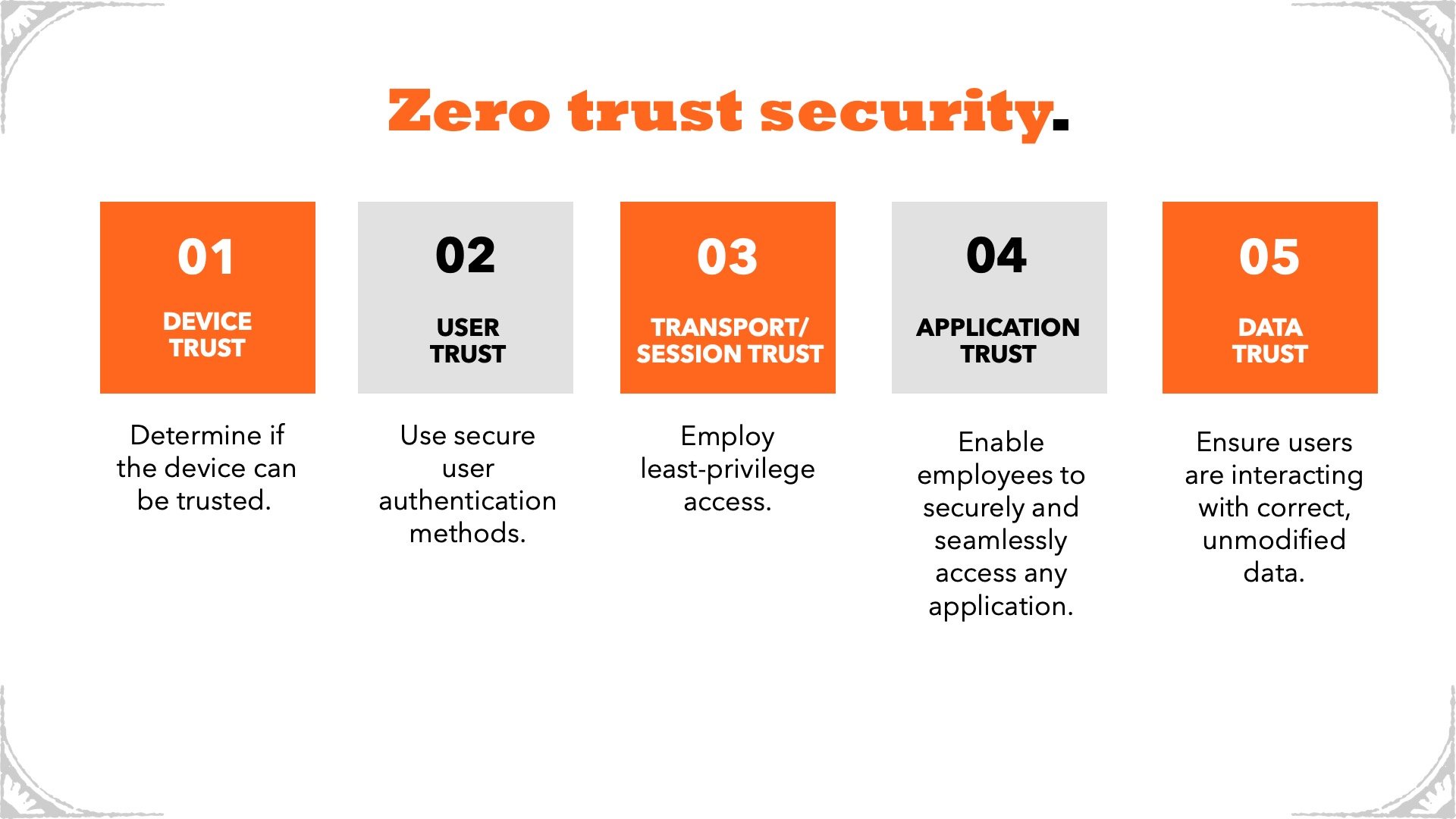
There are five main pillars of Zero Trust security: device trust, user trust, transport/session trust, application trust, and data trust.
- Device Trust - Trusting devices starts with knowing what you have. The best approach involves taking inventory of all devices and solutions required to monitor, manage, and control them. Once that’s complete, you can analyze if a device can be trusted and is compliant with your organization’s security policies.
- User Trust - Employing secure user authentication methods, like multi-factor authentication and conditional access, should be top of mind to establish user trust.
- Transport/Session Trust - The concept of least privileged access, a key component of Zero Trust, means a user or system has access to only those resources specifically required to perform a certain task.
- Application Trust - Especially important in today’s remote work environment, application trust enables employees to easily, securely, and seamlessly access any work application from any device.
- Data Trust - Data trust ensures organizations protect against data leaks and breaches, and users interact with the correct, unmodified data.
Why Zero Trust Should Be a Top Cybersecurity Priority Today

Dan Watson, global senior managing consultant, infrastructure and endpoint security at IBM, argued that today’s melting perimeter represents an opportunity for CISOs to ensure the right user, with the right conditions, has the right access to the right data. By doing so, organizations can move from a disjointed security approach to something more mature.
NIST’s guidance on Zero Trust signals a movement toward awareness and adoption of this security model, Watson explained.
Zero Trust allows cybersecurity professionals to pull together a program and say, "Just because you're inside my network, doesn't mean I trust you." Additionally, with people working from home, coffee shops, and vacation rentals, Zero Trust trust is more important than ever, Watson asserted.
Why Zero Trust Should Not Be a Top Cybersecurity Priority Today

Craig Goodwin, chief product and strategy officer at Cyvatar.ai, argued that Zero Trust shouldn’t be the top priority. For it to be effective, there are plenty of other items that a CISO needs to do first, like IT asset management. How can a CISO focus on Zero Trust when they don't even know what assets exist within the organization?
Additionally, the average tenure for CISOs is between18 and 26 months. Zero Trust is too complicated and complex to make any significant inroads within that time frame, Goodwin argued. Besides, when the next CISO comes in, they’ll have a different approach altogether.
Finally, to implement Zero Trust, a CISO has to influence many people across the organization.. Goodwin argued there are better things to spend time on that’ll yield a bigger bang for each buck, and help focus on risk-reducing initiatives for the organization.




