Introducing Axonius Identities: Tame the Identity Attack Surface in One Place

Ivan Dwyer
Product Marketing, Axonius

We’re excited to announce the expansion of the Axonius Asset Cloud with a new product in our portfolio – Axonius Identities.
IAM programs that span IT and Security teams must deal with the fact that identities are the most dispersed set of artifacts to manage and the most exploitable attack vector to secure.
The fundamental challenge is that no single identity source of truth is the one true identity system of record. Each respective directory, system, and application is only capable of understanding the account, policy, and access model within its own walls. Yet identities don’t exist in isolation, making management efforts disjointed as they extend across systems. And identity-centric threats don’t happen in isolation, they’re the result of toxic combinations of weak posture, blind spots, and potential exploits.
Axonius aims to address the fragmented identity landscape with unified identity data and one place to take action – bringing our market-leading strengths in cyber asset intelligence into the realm of identity intelligence.
Solving Fragmented Identity Challenges the Axonius Way
We have a storied history of helping our customers make actionable sense of their cyber asset and SaaS application attack surface. We’ve learned along the way what it actually takes to effectively close coverage gaps, address blind spots, reconcile conflicting data, remediate misconfigurations, and manage risk across an entire environment.
The identity attack surface mirrors the cyber asset attack surface but requires a different approach to actionability. Identities are in constant motion – their hygiene isn’t determined by a single setting or policy but by how relationships, behaviors, and entitlements intersect in ways the status quo isn’t able to track.
One Data Pipeline For Holistic Identity Operations
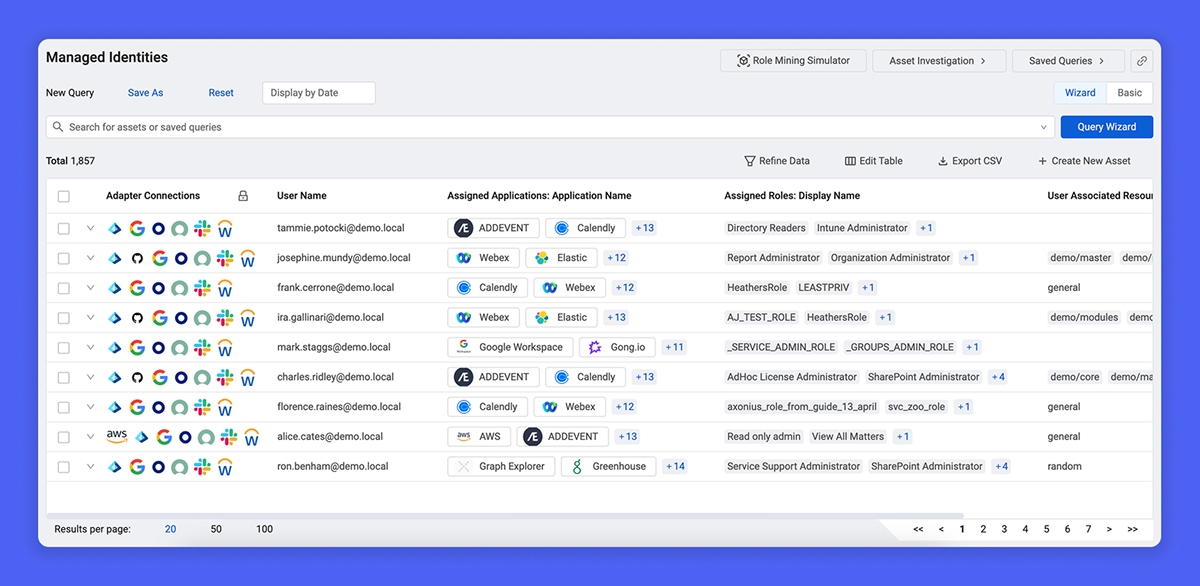
Most organizations don’t have only an identity management problem – they first and foremost have an identity data problem.
Axonius fixes the identity data problem at the foundation – building a complete, accurate, and always up-to-date model of your entire identity fabric. We don’t just aggregate identity data – we correlate, normalize, and associate every identity artifact we collect, and all of that without the need even to rely on SCIM.
In doing so, we’re able to calculate a given identity’s effective permissions – the actual conditions under which a user can access a resource and perform a task. Without this complete view, how else could you be sure that a user was deprovisioned across all systems, that access policies applied consistently, or that MFA was enforced everywhere it should be?
With Axonius Identities, you gain a consolidated identity data model as the foundation for your IAM program:
Complete, accurate, and up-to-date profiles of every human and non-human account
A consistent model of all group memberships, role assignments, and entitlement grants
Powerful search and discovery using a flexible query language and custom dashboards
Dynamic visualizations for permission analysis and role mining exercises
Identity Lifecycles Bring Truth to Action
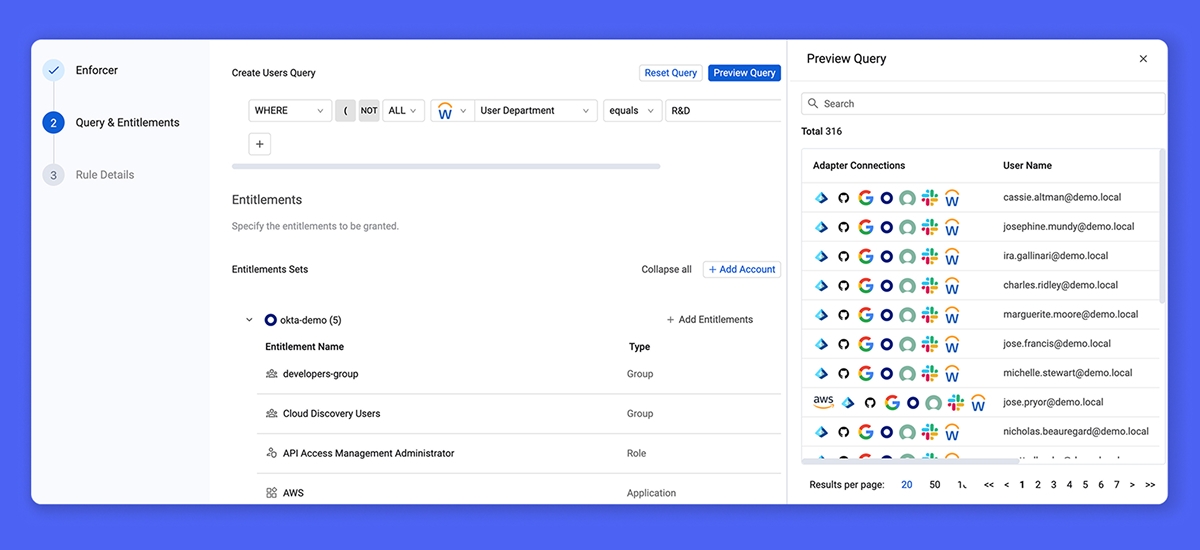
The end game of identity operations is enforcing invariants – what should be true is always proven to be true.
Every joiner, mover, and leaver scenario should trigger identity updates everywhere, instantly – but today, it rarely covers all the bases. The problem isn’t just disconnected or disjointed systems – it’s that each system can only manage the identities and resources it knows about and can interface with. When no single source governs the full identity fabric, accounts get left behind, entitlements become misaligned, and security gaps emerge, forcing teams into an endless cycle of manual reconciliation.
Axonius solves this with direct integrations across every directory, database, system, and application, ensuring identity updates happen all at once. But integrations alone aren’t enough – shifting to Rule Management is the breakthrough that changes how policies are enforced.
Unlike static Role-Based Access, which requires constant tuning and coordination, Rules define identity conditions that must always be true. A Rule in Axonius is a policy-driven enforcement mechanism that ensures identities, entitlements, and access continuously adapt to lifecycle changes. Set the policy once – who should have access to what and under what conditions – and our Rule Engine enforces it across the board, automatically.
And because Axonius sees the full identity landscape, we also use AI to suggest Rules based on real-world analysis of identity relationships, entitlements, and behaviors. For example, if a team consistently shares the same applications, groups, and entitlements, Axonius surfaces this as a recommendation you can apply. As you shift away from Roles to Rules, you’ll notice that over time, Rules replace the need for constant adjustments and permission cleanups – reducing sprawl and simplifying what you actually have to manage.
With Axonius Identities, you gain a comprehensive identity lifecycle management solution for every scenario:
A workflow designer to streamline responsive actions to identity lifecycle events
A rule engine to define entitlements based on a set of conditions
Rule enforcement that monitors lifecycle events to ensure conditions are met
AI recommendations based on entitlement and behavioral patterns
Right-Sized Identity Governance for Right-Sized Access
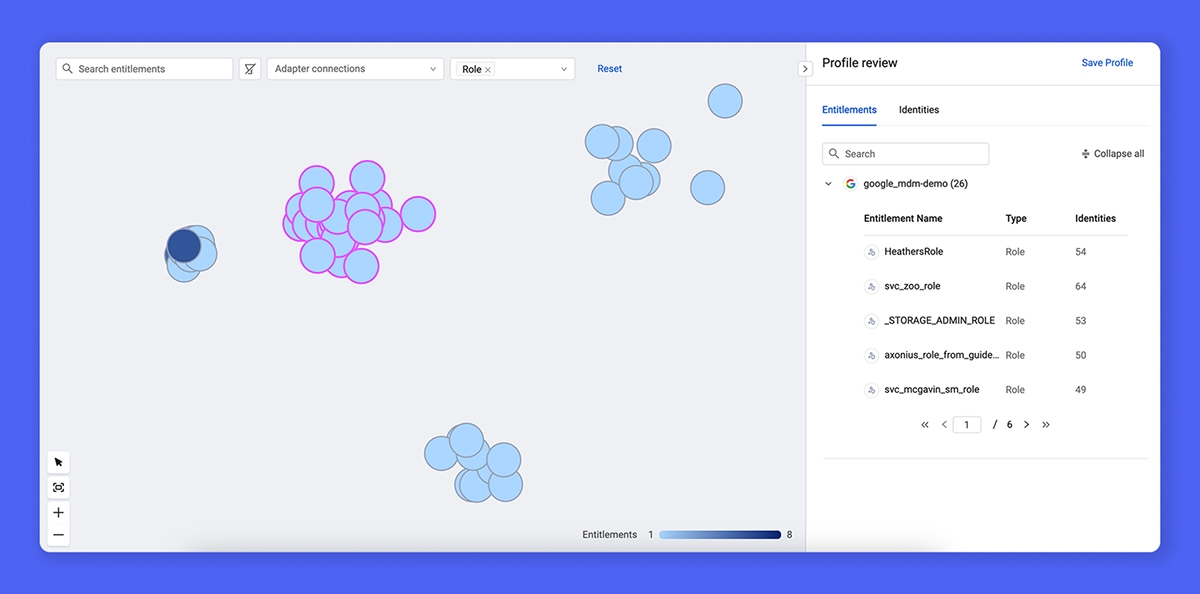
A patchwork of governance solutions can’t govern the whole identity fabric – policies only have power when they’re applied universally.
You know the story – traditional identity governance solutions are heavy, slow, cumbersome, and not built for dynamic environments. They’re super expensive, take forever to implement, and still leave many gaps. Meanwhile, "Light IGA" solutions sound good in theory – until you realize they don’t enforce everything that needs to be enforced and don’t analyze everything that needs to be analyzed. The result? Governance is either too bloated to be effective or too weak to matter.
With complete data and a rule-based model, governance isn’t just easier – it’s more precise, consistent, and enforceable. Role mining becomes actionable, revealing not just how access is assigned, but how it should be controlled. Rules ensure policies aren’t just suggestions – they’re enforced automatically, without constant tuning and coordination. Access requests are validated against enforceable policies, ensuring right-sized access by design. And certifications become effortless, powered by continuously updated identity truth, not static snapshots.
With Axonius Identities, you gain a comprehensive identity governance solution fit to your organization:
Role mining visualization and recommendation engine
Fine-grained permission analysis and optimization
Flexible and automated access requests workflows
Comprehensive access certification campaign management
The Identity Security Flywheel in Motion
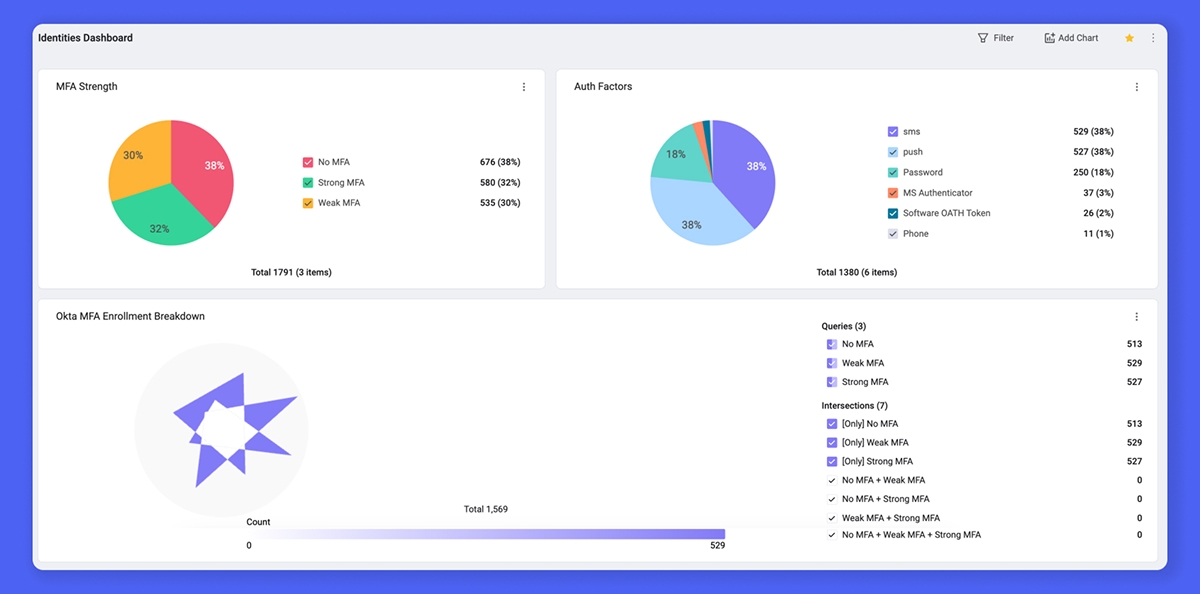
Identity-centric exposures don’t happen in isolation – identity security must be a continuous loop of proactive, preventative, and reactive efforts.
Yet, most identity security solutions operate in silos – limited to compensating controls within their own domains while missing the toxic combinations that create real risk. An over-permissioned account may seem harmless until a misconfiguration exposes it. A lack of MFA may not be concerning until that account is targeted. Without full visibility across the entire identity attack surface, security teams are often left drowning in suspicious activity alerts instead of eliminating the root causes of identity risk.
To secure identities effectively, organizations need a complete view of their identity fabric alongside real-world attack surface signals and posture. Axonius unifies these insights, transforming fragmented identity security efforts into a continuous loop of prevention, detection, and response – ensuring that security teams can optimize posture, close gaps, and contain threats before exposures turn into exploits.
With Axonius Identities, you gain comprehensive identity security without having to buy multiple ISPM and ITDR tools:
Actionable insights into exposures, misconfigurations, and inefficiencies
Real-time user behavior enrichments and analysis
Continuous posture assessment and policy validation
Full visibility into a given identity’s impact and reach
Getting Started with Axonius Identities
Identity sprawl isn’t just an operational headache – it’s an open invitation for misconfigurations, over-permissioned accounts, and ungoverned access to spread across the organization. The status quo leads to more manual work, more alerts, and more risk.
Axonius Identities changes that. Unlike traditional IGA platforms that take months to deploy and years to fine-tune, it delivers value fast – without the heavy lift. No bloated implementations. No armies of consultants. And while point security tools are effective at what they do, they add operational overhead and expand the attack surface. Just like management and governance, identity security needs consolidation to be truly effective.
That’s why Axonius Identities doesn’t just surface identity risk – it enforces what should be true, continuously and universally. By unifying identity data, automating policy enforcement, and aligning access with governance, Axonius eliminates the gaps attackers exploit and the complexity teams struggle to manage.
No more blind spots. No more inconsistent policies. No more identity chaos.
Because in identity, what should be true must always be true – and Axonius makes sure it is.
Categories
- Axonius News

Get Started
Discover what’s achievable with a product demo, or talk to an Axonius representative.
