In May 2023, the National Institute of Standards and Technology (NIST) developed new guidance for federal agencies aimed at helping establish a federal vulnerability disclosure program. Titled, “NIST Special Publication (SP) 800-216: Recommendations for Federal Vulnerability Disclosure Guidelines,” the publication offers a suggested framework for how federal agencies should accept, assess, and manage vulnerability disclosure reports. The publication aligns with the Cybersecurity and Infrastructure Security Agency’s (CISA) Binding Operational Directive 20-01 released in 2020, which required all federal civilian executive branch agencies under CISA’s authority to develop vulnerability disclosure policies.
Vulnerability management is a struggle for nearly every organization, but especially the federal government, for two primary reasons. First, more vulnerabilities exist than the time or resources available to remediate them. In 2016, the Department of Defense Cyber Crime Center, known as DC3, started its own vulnerability disclosure program. In the seven years since then, DC3 has issued 45,000 vulnerability disclosure reports. And NIST previously shared that 20,000 new vulnerabilities were reported to its National Vulnerability Database (NVD) in 2021 alone.
Second, beyond the sheer volume of vulnerabilities, prioritizing which ones need to be remediated first remains equally challenging. Many organizations simply lack the right data and the right context about vulnerabilities in order to make informed decisions.
The first step forward
To help improve federal agencies’ ability to discover, triage, and prioritize vulnerabilities, NIST SP 800-216 highlights the creation of two new government entities: the Federal Coordination Body (FCB) and Vulnerability Disclosure Program Offices (VDPOs). Together, the FCB and VDPOs will work closely with agencies to manage the entire vulnerability disclosure process, from identification to remediation.
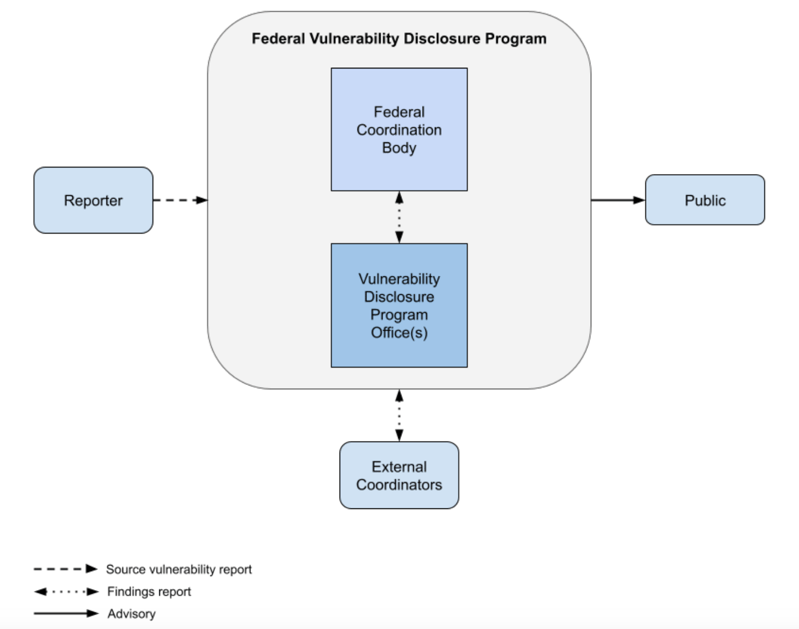
The FCB will act as the “primary interface for vulnerability disclosure reporting and oversight”, whereas VDPOs are defined as “an operational unit that is responsible for information technology (IT) systems and coordinating with other actors to identify, resolve, and issue advisories on reported vulnerabilities.”
VDPOs will also be responsible for identifying the potentially vulnerable technologies and IT systems mentioned in any disclosure report. But SP 800-216 makes sure to highlight that it might take “multiple iterations of discovery and research before a determination can be made” regarding the location of a particular vulnerability. And that’s because the tools that most IT and security teams rely on for vulnerability context, IT asset inventories, are often out-of-date and unreliable.
A key component of vulnerability management
According to NIST SP 800-216, each vulnerability disclosure report should aim to include:
- Product or service name and affected versions
- An identified host or its network interface
- Class or type of vulnerability, optionally using a taxonomy like CWE (Common Weakness Enumeration)
- Possible root cause (or CVE if known)
- Proof-of-concept code or other substantial evidence
- Tools and steps to reproduce the vulnerable behavior
- Impact and severity estimate
- Scope assessment and other products, components, services, or vendors thought to be affected
- Disclosure plans (specifically, embargo and publication timelines)
But obtaining each of these details in a quick and efficient manner would be near impossible without a modern cybersecurity asset management solution. Understanding the assets in an environment and correlating each asset to a specific user are just a few first steps in any vulnerability and risk management process, and they’re also the most critical. Asset visibility helps uncover the relationships between unique vulnerabilities and devices, installed software, and their users.
Specifically, the Axonius Vulnerability Management Module provides extensive visibility to Common Vulnerability Exposures (CVEs) on all devices in an environment. It also includes data enrichment from the CISA Known Exploited Vulnerabilities (KEV), NIST NVD, and other third-party threat intelligence sources.
Axonius enables agencies to better enforce vulnerability disclosure programs through the use of better contextual data that helps understand and assess urgency, relevancy, significance, and importance of vulnerabilities.
The future of vulnerability disclosure
The NIST SP 800-216 is one of two publications the agency is working on to improve incident reporting and vulnerability disclosures to “minimize the unintended exposure of government and private information, the corruption of data, and the loss of services.” But building a successful vulnerability disclosure program requires cybersecurity asset management. Without it, the ability to determine which assets are most at risk and in need of urgent remediation will be far too challenging for any IT or security team to carry out.




